Stealthy Information Stealers Leveraging Trusted Platforms and Non-Traditional Execution Methods
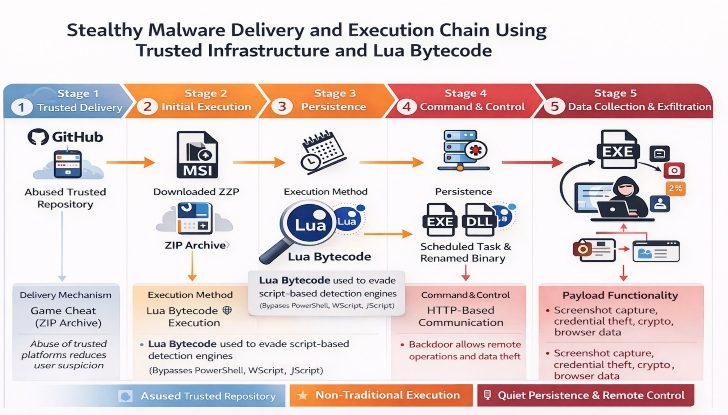
Modern information-stealing malware continues to evolve toward greater stealth, flexibility, and abuse of trust. One notable evolution is the use of non-traditional execution methods, such as Lua bytecode, to conceal malicious logic and evade common detection mechanisms. By avoiding heavily monitored scripting engines and recognizable malware patterns, attackers significantly reduce their operational footprint while maintaining full control over compromised systems.
Information stealers of this class are typically designed to harvest a wide range of sensitive data, including credentials stored in web browsers, cryptocurrency wallet information, VPN credentials, payment data, and system or network identifiers derived from IP addresses. Their modular design allows them to be easily adapted and reused by different threat actors, contributing to their widespread and persistent presence across regions and industries.
A recurring tactic in these campaigns is the abuse of trusted infrastructure for malware distribution. Rather than relying solely on overtly malicious hosting, attackers increasingly leverage reputable platforms—such as software repositories, development tools, and open-source ecosystems—to host or deliver payloads. This approach exploits the implicit trust users place in well-known platforms and complicates detection, as security controls are often less aggressive toward high-reputation domains.
Social engineering remains a core component of delivery. Malware is frequently disguised as legitimate software, such as productivity tools, utilities, or game enhancements, to entice users into execution. In some cases, victims are encouraged to share the software with others, turning initial compromises into secondary distribution channels and amplifying reach without direct attacker interaction.
Once executed, these malware families commonly establish persistence through native system mechanisms, such as scheduled tasks or service registrations, while renaming or re-launching binaries to hinder analysis. Command-and-control communications are typically conducted over standard protocols, allowing malicious traffic to blend in with normal network activity. Rather than acting solely as passive stealers, many variants function as backdoor platforms, capable of executing remote commands, collecting additional data, and dynamically extending functionality.
These techniques reflect broader, long-standing trends in the threat landscape:
Evasion over exploitation: Attackers increasingly prioritize stealth and longevity over noisy exploitation.
Trust abuse over brute force: Reputable platforms and legitimate tooling are weaponized to bypass user skepticism and security controls.
Behavioral flexibility: Malware adapts its execution, persistence, and communication methods to suit the target environment.
Blurring consumer and enterprise targeting: Techniques proven effective against individuals are rapidly repurposed for organizational environments.
For defenders, these developments reinforce the importance of behavior-based detection, execution monitoring, and identity-centric security controls, rather than reliance on static indicators or signature-based approaches. Equally critical is user awareness of social engineering tactics and tighter governance over the execution of untrusted or unofficial software, even when sourced from seemingly legitimate platforms.