As an investor, I’ve spent years talking to hundreds of entrepreneurs and dozens of practitioners attempting to solve the modern data security problem. Data in the enterprise is a double-edged sword: On one hand, today’s enterprises need to derive value from ever-growing quantities of data. The most successful will be the enterprises in which all employees are equipped to efficiently leverage data to make data-driven decisions. This requires high levels of data collaboration and expanding data access. On the other hand, expanded data collaboration and access leads to an expanded attack surface, increasing the enterprise risk posture and exposing the enterprise to cybersecurity threats.
The challenge is to find a balance of visibility, accessibility, and data controls. Traditionally, CISOs have been gatekeepers tasked with preventing the flow of data throughout their organizations. CISOs use legacy tools designed for centralized, coarse-grained access controls that provide limited visibility across hybrid environments that are simply not built for modern enterprise data needs. Without effective ways to see and collaborate on data, data is frequently shared via copies that cause data sprawl and shadow data, further reducing visibility, increasing risk, and compounding the problem. For the 2023 CISO Survival Guide to Emerging Trends from the Startup Ecosystem (in partnership with Cisco Investments, NightDragon, and Team8), we spoke with practitioners and conducted a poll of over 100 security leaders to hone in on issues around identity, data and collaboration, software supply chain, and cloud security.
At the moment, we’ll focus on structured data objects (e.g., databases) and exclude file management and file sharing.
Visibility: A Blueprint for the Future of Data Security
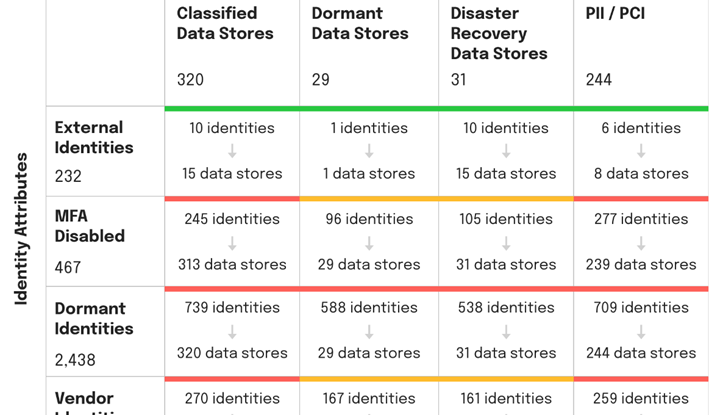
In our CISO Survival Guide, data access control was flagged as the second highest priority for security hygiene spending, behind data identity and privileged access management. It’s no surprise that the first step in securing data in the modern enterprise is at the intersection of data and identity and the ability to answer these two questions:
Tools that highlight different identity attributes vs. data store attributes and enable CISOs and compliance teams to see and remediate overprivileged access to on-premises and cloud data stores can be helpful. Such views are essential to developing sophisticated visibility into crown-jewel data across your hybrid environment. The ability to double-click into the details and see who has accessed what data and when is a powerful tool for compliance and post-breach investigations.
Modern Data Security: The Roadmap to Secure Data Collaboration
Enterprises need to start thinking about how they will improve data collaboration across data stores throughout the enterprise. Data security must simultaneously improve risk management and enhance usability. From my perspective, there are a few key concepts that need to be enabled to enable data collaboration:
While companies will have their unique journeys that require contextualized decision-making, I recommend companies approach collaboration at the line-of-business level, unlocking data collaboration in smaller segments of the enterprise that will lead to an exponential impact over time. Companies and security teams that cling to legacy data security and are too slow to adopt modern practices will fall behind. Agility, accessibility, and security are table stakes for enterprises of the future to leverage data and drive business.