
The prolific hacking group made up primarily of young people that was behind a recent breach that crippled several Las Vegas resorts has made graphic threats of violence as part of its attempts to force victims to give up their credentials, according to research released Wednesday.
According to researchers with Microsoft’s threat intelligence and incident response divisions, members of the group it tracks as Octo Tempest — also known as 0ktapus, Scattered Spider or UNC3944 — tends to first target technical personnel on support desks and use social engineering techniques to trick them into giving up credentials or granting access to protected systems.
But in some cases, the group has come to rely on violent threats to break into high-profile targets, including in at least one incident sending text messages threatening violence against a target’s wife.
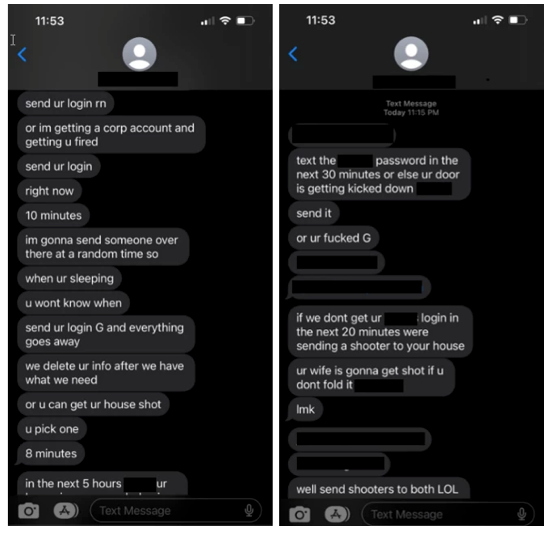
Made up primarily of native English speakers in their teens and early 20s, Scattered Spider represents what Microsoft’s researchers describe as “one of the most dangerous financial criminal groups” working online today, capable of “broad social engineering campaigns to compromise organizations across the globe.”
Researchers began to take notice of the group in early 2022, as its members became increasingly involved in SIM swapping and account takeovers to facilitate cryptocurrency theft. By early 2023, some members of the group developed a more advanced, aggressive approach and began monetizing the extortion of telecommunications, email and technology organizations.
While researchers refer to the criminal collective as a group for ease of tracking, it emerged from a larger ecosystem that refers to itself as “the Com.” This community of disparate subgroups and cliques include people engaging in account takeovers, SIM swapping, cryptocurrency thefts and occasionally violence for hire.
The Com rocketed to public attention after striking Caesars Entertainment and MGM Resorts last month in an operation that crippled casino and hotel operations. But that attack was merely the latest in a string affecting major corporations, including Okta, Microsoft, Nvidia, Rockstar and Samsung, researchers have said.
A cybersecurity researcher familiar with the Com, who spoke on condition of anonymity given the group’s history of violent threats, said that the cybersecurity industry has failed to address the group with sufficient urgency. The people involved in this activity are “creative in ways the industry doesn’t give them credit for,” the researcher said. “Refusal to take kids seriously is why we have gotten so far into this mess.”
Microsoft’s researchers caution that the Com appears to be collaborating with other, more well-established criminal groups. By mid-2023, some members established an affiliate relationship with the ransomware group ALPHV/BlackCat and used the group’s leak site to post victim data.
More recently, some Com members have displayed “a diverse array” of techniques, tactics and procedures to “navigate complex hybrid environments, exfiltrate sensitive data, and encrypt data,” the researchers wrote.
But the group is best known for its uncanny ability to use social engineering techniques to convince its targets to give up their credentials. In attacking Caesars and MGM, the group tricked a help desk worker into providing access to protected networks and then exploited that access to extort the resort giants.
Caesars reportedly paid roughly $15 million to the attackers, the Wall Street Journal reported at the time. MGM refused to pay but suffered more than $110 million in direct and indirect costs and losses from the incidents, according to federal filings.
The post Hackers that breached Las Vegas casinos rely on violent threats, research shows appeared first on CyberScoop.