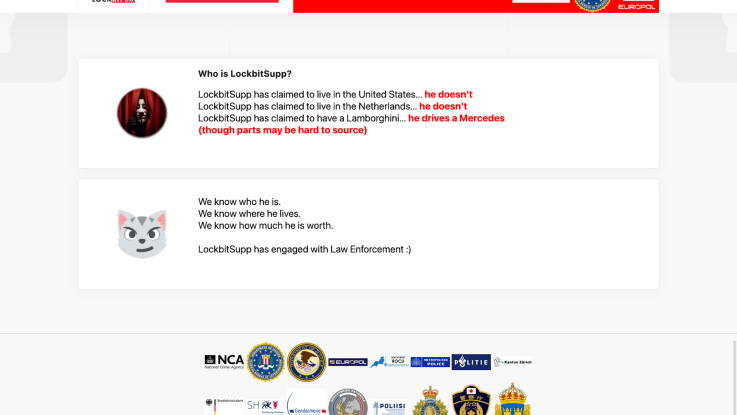
After LockBit takedown, police try to sow doubt in cybercrime community After seizing the digital infrastructure of the ransomware group LockBit earlier this week, the law enforcement agencies behind that operation have carried out an unusual messaging campaign designed to create questions in the minds of criminal hackers about the presence of infiltrators in their midst. On Monday, security researchers focused on cybercrime noticed that the Federal Bureau of Investigation together with the U.K.’s National Crime Agency and a host of other law enforcement agencies had apparently seized the main website used by LockBit, the world’s most prolific ransomware operator, to shame its victims into paying exorbitant extortion demands. As part of the operation, police replaced the clickable links that previously linked to LockBit victims’ data with their own links, including one to a press release and others announcing sanctions, arrests, indictments and decryption information. Tantalizingly, the site included a link promising that information would be released Friday about the head of LockBit, a persona known online as “LockBitSupp.” Friday’s reveal did not expose his identity, but police say they know who he is, where he lives and how much he’s worth. As if to twist the knife, police said that LockBitSupp “has engaged with Law Enforcement” — without specifying what they meant. The National Crime Agency declined to answer questions about Friday’s post related to LockBitSupp’s identity. Experts and longtime observers of LockBit say the message — as well as the overall strategy of taking complete control of LockBit infrastructure and exposing its affiliates — aims to both undermine trust in LockBit among the cybercrime ecosystem and potentially provoke a response from the leader himself. “This is a psychological operation, and I have been begging anyone who will listen to me to implement doing these [types] of mitigation strategies,” said Jon DiMaggio, chief security strategist for Analyst1. Doing so, DiMaggio argued, can seed “doubt in the minds of other cyber criminals who will be less likely to trust LockBit and work for him.” DiMaggio and his colleagues have reported extensively on LockBit activities and carried out interviews with LockBitSupp that reveal a confident character who cares about his reputation and how he is perceived. That confidence seems to fuel a belief that he can operate in perfect anonymity: In January, he offered a $10 million reward to anyone who could reveal his identity. DiMaggio said the law enforcement’s messaging campaign seems “designed for him.” Kurtis Minder, the co-founder and CEO of GroupSense and a longtime ransomware negotiator, told CyberScoop that his dealings with LockBit representatives over the years suggest that LockBitSupp is “volatile,” and that the messaging campaign may be an intentional provocation “to get him to say something stupid” that might be used against him. By insinuating that LockBitSupp is working with law enforcement in some undefined capacity, the messaging campaign also seeks to create suspicion between LockBit and the affiliates that pay handsomely to use its services. “Law enforcement is sowing the seeds of distrust,” Alexander Leslie, an intelligence analyst with Recorded Future, said Friday in a post on X. “As if the actions of the last week weren’t enough… now affiliates have to be concerned that LockBitSupp is not only a liar, but a snitch.” Allan Liska, a threat intelligence analyst at Recorded Future’s Insikt Group, told CyberScoop in an email Friday that the police message about communicating with law enforcement could be interpreted in two ways. First, it could imply that LockBitSupp is an informant for law enforcement, an accusation Liska said has been made by other ransomware gangs, including the group known as ALPHV, who have a clear motive in trying to denigrate a rival. Or, Liska said, “law enforcement may have infiltrated LockBitSupp’s inner circle and LockBitSupp may have been unwittingly sharing sensitive information with law enforcement.” Either scenario would devastate trust in LockBitSupp as he tries to reconstitute his operation, Liska noted. In combating online crime, law enforcement agencies are also realizing that they need to win a PR battle against groups that historically have operated with impunity and mocked their opponents online. By seizing their website and using it to promote material that is harmful to LockBit’s criminal enterprise, law enforcement is “turning their tools against them,” Adam Hickey, the former deputy assistant attorney general with the Department of Justice’s National Security Division, told CyberScoop. “Law enforcement recognizes that if they are to be seen as effective, their disruption needs to sell, it needs to land as impactful,” Hickey said. “I think that splash page is just an attempt to make this more marketable.”