LAS VEGAS — 5G commercial networks are starting to roll out, promising exciting new use cases like automated cars, and smart sensor networks where the nodes have 10-year battery lives. To go along with these possibilities are new security requirements; notably, improvements in device authentication, traffic encryption, privacy protections for device IDs and credentials,and improvements in resilience and integrity.
Click to enlarge.
However, many of the security protocols and algorithms for 5G are being ported from the previous 4G standard, which researchers have found can still allow device fingerprinting for targeted attacks as well as the possibility of man-in-the-middle (MiTM) offensives.
By way of background, 5G network architecture is made up of base stations (either macro or small-cell, depending on the application), which, like 4G cell towers, cover a specific area. These base stations connect to a mobile edge cloud, which in turn connects to the core network. In order to connect to a carrier network, 5G devices send a raft of information to the base station, which passes it on along the chain for eventual registration and authentication to the core network.
The components inside devices allow different capabilities depending on what the device is used for, and according to Altaf Shaik, a graduate student at the Technical University of Berlin and Kaitiaki Labs, it’s this information that gets sent to the base station. It includes things like whether or not voice calling is enabled, SMS ability, vehicle to vehicle communication (V2V) support, what frequency bands are being used, the device category (there are 20 of these, corresponding to the processing power of the device), and radio requirements, like whether the device needs the radio access network (RAN) to use MIMO to boost throughput speeds.
At a session at Black Hat 2019 called “New Vulnerabilities in 5G Networks,” presenting research he carried out with his partner, Ravishankar Borgaonkar of SINTEF Digital, Shaik noted that in 5G, as with 4G, the device capability information is sent to the base station before any security is layered onto the connection. Over-the-air security includes encryption of traffic from the endpoint to a base station; but since the device capabilities are transmitted prior to that kicking in, they are visible in plain text.
This, according to Shaik, enables three kinds of attacks: Mobile network mapping (MNmap); bidding down; and battery drain on narrowband Internet of Things (NB IoT) devices.
Using real devices and commercial networks in Europe and the U.S., the research team was able to sniff the information sent by the device in plain text, and use it to create a map of devices connected to a given network.
“We set up a fake base station to receive the capabilities of all the devices,” he explained. “We categorized maker, model, OS, use case and version. This allows you to identify any cellular device in the wild. You can tell if a device is Android or iOS, if it’s IoT or a phone, if it’s a car modem, a router, a USB dongle a vending machine, etc.”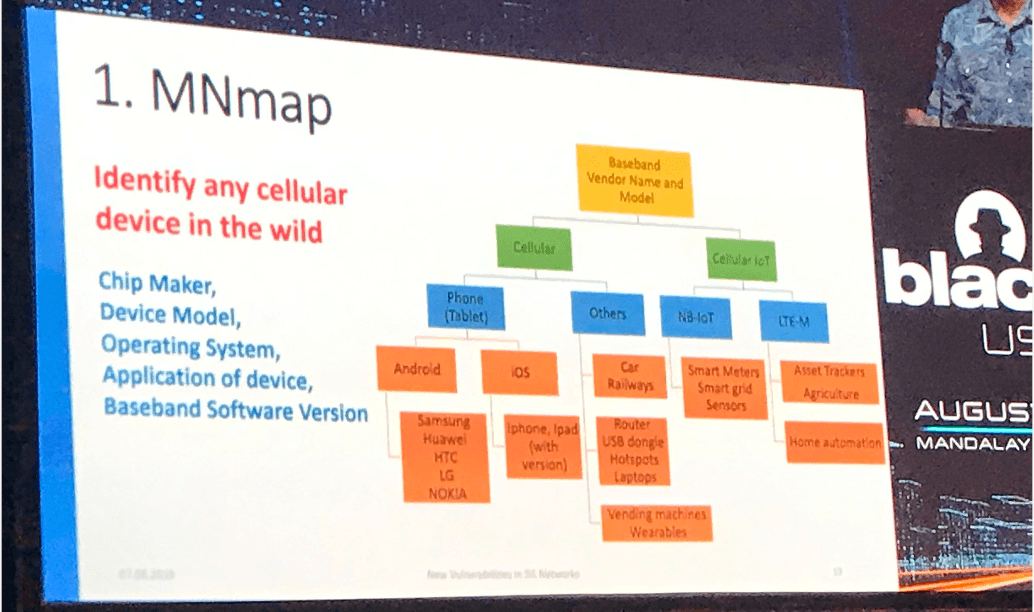
That in turn paves the way for targeted attacks against a specific device or a whole class of devices, he added. “You can plan a targeted attack against a certain kind of device – such as those used in field testing, or military devices. There’s also a privacy aspect here because you can link the IMSI to a specific person.”
Making these identifications is possible in part because there are five main baseband manufacturers that implement certain capabilities used in endpoint hardware: Intel, Huawei, Mediatek, Samsung and Qualcomm. Not all capabilities are mandatory, so knowing what each baseband manufacturer enables can help fingerprint a device. A feature called EIAO for instance is typically disabled in Qualcomm but not in the others.
“Once you know the baseband maker, you can tell what kind of modem the device uses, and you end up with a list of devices that use those modems,” explained Shaik.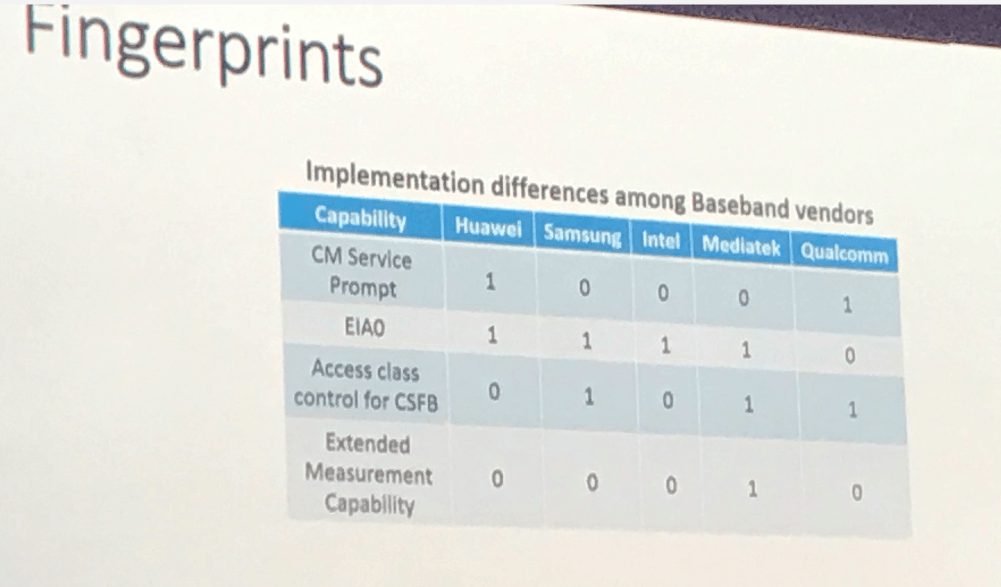
At the same time, deductive reasoning using the rest of the data can be applied, given that different use cases require a different set of capabilities. Cars only need access to V2V, for instance; mobile phones need voice codecs; and IoT sensors need power saver mode enabled to protect their battery life.
“This allows you to do a fair amount of fingerprinting,” explained Shaik. “We collected the capabilities and created a reference model showing the baseband vendor, application, chipset name, 3GPP release.”
MiTM Attacks
In addition to MNmap, the bidding-down and battery-drain attacks become possible by implementing a MiTM relay to hijack the device information before security is applied, as it’s being sent to the base station.
“You can take this data and modify the capabilities,” Shaik said. “For instance, the RAN defines the speed a device receives. An iPhone is supposed to receive speeds up to 1Gbps. You can change the device category so the RAN doesn’t think it’s an iPhone and instead delivers only 2Mbps, let’s say.”
In bidding down, adversaries cut off the capabilities of high-end devices. Attackers can remove carrier aggregation or MIMO enablement, which are used to boost speed; they could alter the frequency band information for a device to prevent handovers or roaming; or they could disable voice over LTE, which makes a phone revert to 3G/2G voice calling.
Worse, the core network saves the capabilities for a device until it’s restarted, giving the attack a persistence dimension.
In testing, 22 out of 32 tested LTE networks worldwide were vulnerable to these types of attacks, Shaik said, with most of the tampering persisting for an average of seven days.
The battery drain attack is targeted at NB-IoT devices, which are low-power sensors that send limited amounts of information infrequently. They boast a 10-year battery life, enabled thanks to power-saving mode (PSM) that turns them off when not in use.
As a MiTM, an attacker can modify the PSM parameters, removing it altogether. Absent PSM, the device has continuous activity, scanning to find something to connect to. In testing, the researchers found that devices reset after an average of 13 days, reducing the battery life by a factor of five.
After reporting the issues (CVD-2019-0018) to the GSMA, 3GPP and other standards bodies, as well as the vendors, a fix was implemented in Release 14 of the 5G standard, to ensure that security is applied before the device sends its fingerprinting information.
However, it will take a while for this to roll out commercially.
“As far as we can tell, no vendor is actually implementing them yet,” Shaik said. “Release 14 is quite new, so maybe next year we’ll start seeing the fixes.”
For existing 5G networks, MNmap remains possible; the device capabilities need to be protected by implementing mutual authentication before the information becomes accessible.
“This is a problem, a fundamental issue that was ported from 4G,” Shaik said. “But in 5G, there are more use cases and more capabilities that define exactly what kind of device it is, making targeting that much easier.”
Black Hat USA 2019 has kicked off this week in Las Vegas. For more Threatpost breaking news, stories and videos from Black Hat and DEF CON, click here.