Cryptocurrency continues to be a favorite target of attackers, with attacks targeting Bitcoin and other currencies growing at a robust pace.
In the recently released 2023 Data Breach Investigations Report (DBIR), Verizon noted that attacks in its dataset that specifically target cryptocurrency data grew 300% over 2022 to 48 incidents reported, up from 12 the year before. Whether the trend continues this year remains to be seen, says David Hylender, senior manager of threat intelligence for Verizon.
“The crypto boom presented many opportunities for attackers to gain access to many valuable crypto assets,” Hylender says. “However, the circumstances have changed somewhat over the past year, and they may result in corresponding changes in the degree that attackers will be targeting this type of data.”
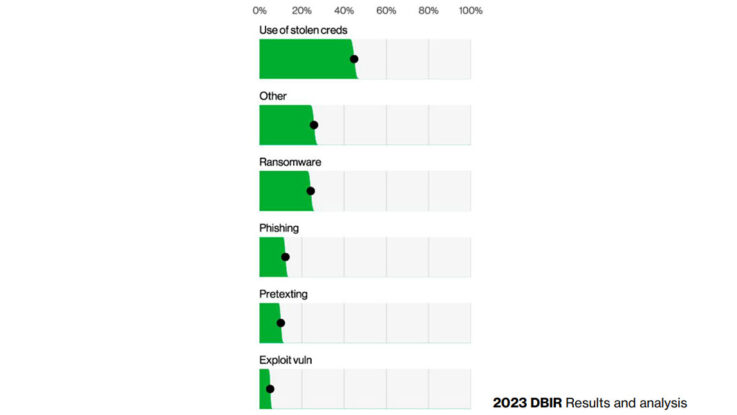
Of the attacks submitted to the Verizon DBIR, about half used an exploit, more than 40% used stolen credentials, and about a quarter incorporated a phishing attack, according to the report. While some of the attacks — more than 10% — used email as a vector, most compromised the user’s account through the Web application or an application programming interface, the report stated.
Verizon’s Hylender cautioned that the company had received only dozens of reports, much smaller than the hundreds or thousands of other types of compromises the company analyzed from other sources.
“We caveat in the report that although it has seen a fourfold increase, it is still a relatively small number compared to all other data types,” he says.
Volatile Markets, Stable Cybercrime
Over the past decade, cryptocurrency has become an integral part of the cybercriminal ecosystem, allowing would-be attackers to pay for a variety of offensive-security services and receive payments from ransomware victims. Increasingly, the potential for quick and substantial financial gains has attracted speculative investors, who are, in return, targeted by scammers aiming to exploit this enthusiasm for their own benefit, says Kurt Baumgartner, a principal security researcher with Kaspersky.
“Cryptocurrency enables cybercrime in multiple ways,” Baumgartner says. “We’ve seen cryptocurrency exchanges pilfered, cryptocurrency trading apps trojanized and their related Web sites compromised for use as command and control, cryptocurrency used by cybercrime individuals and groups for employment and services payments, … and cryptocurrency used as an easily laundered method of sometimes massive payment by victims in the millions for ransomware and other extortion crimes.”
Even as the value of cryptocurrency fluctuates wildly in the market, it remains a popular financial instrument for cybercriminals to use and abuse. Last year, the number of cryptocurrency-related phishing attacks targeting Kaspersky customers grew 40% to 5.0 million, up from 3.6 million in 2021, the company stated.
One campaign used a trojanized Tor browser to steal cryptocurrency from more than 15,000 users in 52 countries, stealing at least $400,000, according to Kaspersky’s research. In another campaign, cyber-thieves used a loader dubbed DoubleFinger to install a Trojan — dubbed GreetingGhoul — that replaces the login window of common cryptocurrency wallets with an information-collecting duplicate.
“DoubleFinger, coupled with GreetingGhoul, is an advancement for crime elements both in terms of stealth technology and targeting when it comes to cryptocurrency theft,” Kaspersky’s Baumgartner says. “As cryptocurrency continues to be a highly valued object of online theft efforts, with individuals protecting themselves with cold wallets and the like, malware like these demonstrate serious advancement both in malicious technologies and techniques.”