Apple once again is drawing the line at breaking into a password-protected iPhone for a criminal investigation, refusing a request by the Federal Bureau of Investigation (FBI) to help unlock the iPhones of a shooter responsible for an attack in Florida.
The company late Monday said it won’t help the FBI crack two iPhones belonging to Mohammed Saeed Alshamrani, a Saudi-born Air Force cadet and suspect in a shooting that killed three people in December at the Naval Air Station in Pensacola, Fla.
The decision is reminiscent of a scenario that happened during the investigation of a 2015 California shooting, and could pit federal law enforcement against Apple in court once again to argue over data privacy in the case of criminal investigations.

While Apple said it’s helping in the FBI’s investigation of the Pensacola shooting—refuting criticism to the contrary—the company said it won’t help the FBI unlock two phones the agency said belonged to Alshamrani.
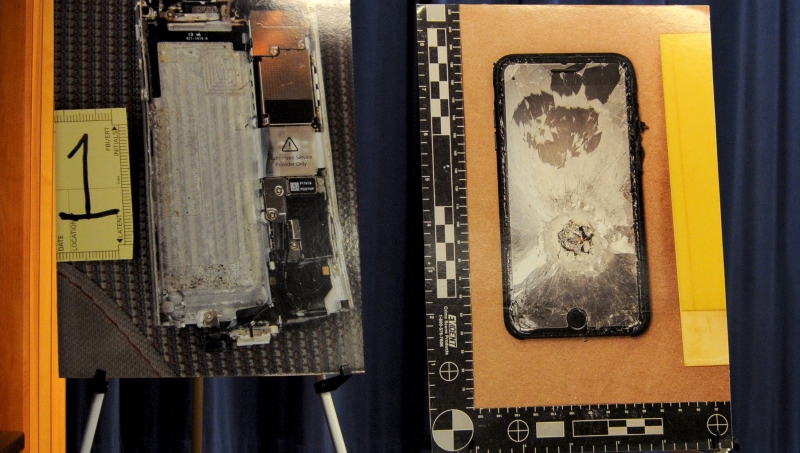
Mohammed Saeed Alshamrani’s iPhone recovered by FBI. Image credit FBI.gov
“We reject the characterization that Apple has not provided substantive assistance in the Pensacola investigation,” the company said in a statement emailed to Threatpost. “Our responses to their many requests since the attack have been timely, thorough and are ongoing.”
Even though Apple won’t help the Feds unlock the devices, the company said it’s been responding “promptly” to requests for assistance and “sharing information with FBI offices in Jacksonville, Pensacola and New York,” according to the statement.
“The queries resulted in many gigabytes of information that we turned over to investigators. In every instance, we responded with all of the information that we had,” the company said. “We are continuing to work with the FBI, and our engineering teams recently had a call to provide additional technical assistance. Apple has great respect for the Bureau’s work, and we will work tirelessly to help them investigate this tragic attack on our nation.”
The FBI sent a letter to Apple’s general counsel last week asking the company to help the agency crack the iPhones, as their attempts until that point to guess the “relevant passcodes” had been unsuccessful, according to the letter, which was obtained by NBC News.
Attorney General William Barr followed up that request with a declaration Monday that the shooting was an act of terrorism and reiterated law enforcement’s plea to Apple to unlock Alshamrani’s phones—an iPhone 7 and iPhone 5. Alshamrani, who is believed to have acted alone, was killed during a shootout with security officers at the base.
“So far Apple has not given us any substantive assistance,” Barr said in a press conference Monday. “This situation perfectly illustrates why it is critical that investigators be able to get access to digital evidence once they have obtained a court order based on probable cause. We call on Apple and other technology companies to help us find a solution so that we can better protect the lives of Americans and prevent future attacks.”
The scenario is similar to one that occurred when the FBI asked Apple to unlock the phone of Syed Farook, one of two men who carried out a shooting attack on a city meeting in San Bernardino, Calif. It also sets up a scenario in which a court could be the deciding factor if Apple must unlock the phones or not.
Though Farook, like Alshamrani, died in a shootout the same day as the attack, the Department of Justice (DoJ) asked for Apple’s help to access the phone’s content, also citing terrorism and national security as its reasons. When the company wouldn’t help, the DoJ took the vendor to court over the issue.
Eventually, a court order demanded that Apple assist in cracking the phone by providing a one-time firmware update–customized for that one device–that would bypass the auto-erase function protecting the phone, which would allow the FBI to brute-force the passcode.
At the time, Apple’s CEO Tim Cook argued that this scenario set a dangerous precedent whereby the FBI could demand a backdoor into any person’s device.
In the end, the FBI unlocked the phone through the help of a third party, which let Apple off the hook. FBI Director James Comey said at the time that the Bureau had purchased a “tool” to hack the phone that cost more than $1.3 million, with the Washington Post later reporting that “tool” was zero-day exploit from “professional hackers.”
It remains to be seen if the FBI will use the same tactics this time or if Apple will be forced by law to come to the Bureau’s assistance.
Concerned about mobile security? Check out our free Threatpost webinar, Top 8 Best Practices for Mobile App Security, on Jan. 22 at 2 p.m. ET. Poorly secured apps can lead to malware, data breaches and legal/regulatory trouble. Join our experts to discuss the secrets of building a secure mobile strategy, one app at a time. Click here to register.