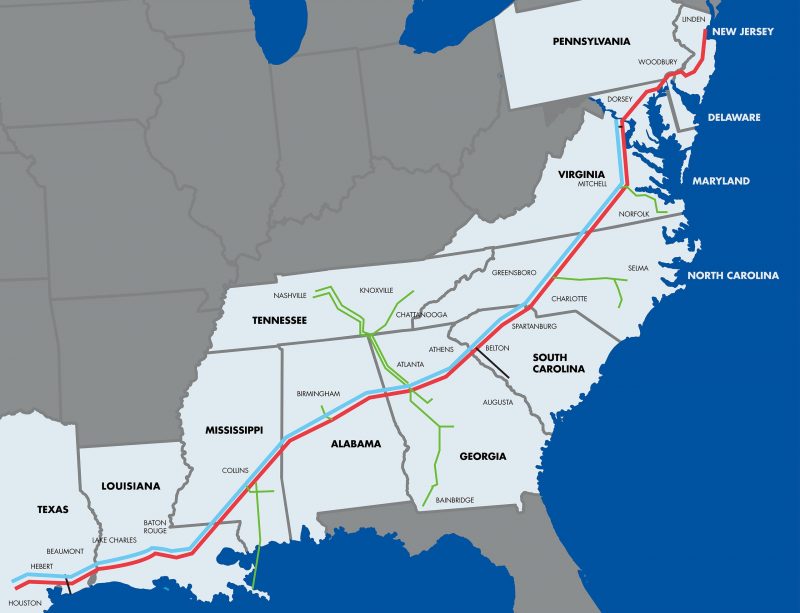
The Biden administration has declared a state of emergency that covers 17 states and Washington D.C. in the wake of the ransomware attack on the Colonial Pipeline Co., and is working with Colonial to restart operations.
On Monday morning, FireEye also confirmed to Threatpost that it’s been called in to help with the investigation, but it wasn’t at liberty to say anything more.
The news comes as security researchers mulled possible perpetrators of the attack, and warned that the incident could be a harbinger of things to come.
The Biden declaration, which the government made on Sunday following Friday’s attack and pipeline shutdown, covers Alabama, Arkansas, D.C., Delaware, Florida, Georgia, Kentucky, Louisiana, Maryland, Mississippi, New Jersey, New York, North Carolina, Pennsylvania, South Carolina, Tennessee, Texas and Virginia. The government is working to keep the supply of gasoline, diesel, jet fuel and other refined petroleum products flowing to those states and the capital.
Join Threatpost for “Fortifying Your Business Against Ransomware, DDoS & Cryptojacking Attacks” a LIVE roundtable event on Wednesday, May 12 at 2:00 PM EDT for this FREE webinar sponsored by Zoho ManageEngine.
As well, the Cybersecurity & Infrastructure Agency (CISA) has posted ransomware guidance and resources, saying that it’s engaged with Colonial over the attack.
Colonial, which moves about 2.5 million barrels of liquid fuels to the eastern and southern U.S. every day, was forced to shut down pipeline operations on Friday. It wasn’t clear at the time whether the digital assault had actually caused the shutdown, but in a statement on Sunday, the company clarified that the shutdown was in fact proactive.
“Maintaining the operational security of our pipeline, in addition to safely bringing our systems back online, remain our highest priorities,” according to Colonial’s statement. “Over the past 48 hours, Colonial Pipeline personnel have taken additional precautionary measures to help further monitor and protect the safety and security of its pipeline.”
This is a massive hit to the country’s infrastructure: Colonial carries 45 percent of fuel supplies to the eastern U.S. About 5,500 miles of pipeline were proactively shut down in response to the attack. As of Sunday evening, Colonials’ operations team was still working on a system restart plan. Its mainlines were still offline, but it had restarted some smaller lateral lines between terminals and delivery points.
“We are in the process of restoring service to other laterals and will bring our full system back online only when we believe it is safe to do so,” Colonial said, “and in full compliance with the approval of all federal regulations. At this time, our primary focus continues to be the safe and efficient restoration of service to our pipeline system, while minimizing disruption to our customers and all those who rely on Colonial Pipeline.”
On Monday morning, Threatpost asked Colonial for an update and will update this article if it responds.
And So Begins a Legacy on Protecting Infrastructure
Lior Div, Cybereason’s CEO and co-founder, told Threatpost on Monday that the attack should be evaluated against the backdrop of the SolarWinds and Microsoft Exchange Server attacks, which have been “unparalleled” in scope, “successfully infiltrating and compromising virtually every U.S. government agency and a wide array of medium and large private-sector companies.”
He echoed a call for an overhaul of critical systems that’s resounded throughout the country since the attack was made public on Friday. “The Colonial Pipeline attack reinforces the need to update legacy systems running today’s critical infrastructure networks,” he said. “How the Biden administration responds to the broader and more wide-scale attacks will be a part of the administration’s legacy.”
Who’s Behind the Pipeline Attack? DarkSide?
Security experts are looking at a few possibilities regarding which ransomware gang is behind the attack, with the top contenders being DarkSide and Ryuk.
Reuters and Bloomberg sources – including a former U.S. official and two people involved in the investigation – said that the intruders belong to the DarkSide gang: A group of professional digital extortionists that’s new to the party but clearly not lacking in criminal expertise. It has hit utility and critical-infrastructure targets in the past.
Div told Reuters on Sunday that DarkSide is made up of veteran crooks who are adept at squeezing every possible dime out of victims. “They’re very new but they’re very organized,” he said. “It looks like someone who’s been there, done that.”
As CyberReason described in a post in early April, DarkSide made its first appearance less than a year ago, in August. The team offers its malware up for lease, following the RaaS (ransomware-as-a-service) model. CyberReason said last month that the DarkSide team recently announced on Hack Forums that it had upgraded its offering, releasing DarkSide 2.0, with the fastest encryption speed on this underground market, DarkSide claimed. it includes Windows and Linux versions.
On Monday, CyberReason told Threatpost in an email that its researchers have seen DarkSide launched against targets in English-speaking countries, and that it appears to avoid targets in countries associated with former Soviet-bloc nations. The group’s ransom demands range between $200,000 to $2,000,000, and like so many similar groups, it throws a superhero cloak over its crimes: In October, the group tried to donate around $20,000 in stolen Bitcoin to two international charitable organizations, The Water Project and Children International, which was announced by a press release on the underground: A gimmick that experts said was likely a publicity stunt. The charities refused to accept the funds.
DarkSide, again like similar Robin Hood wannabes, also reportedly has an ethics code that prohibits attacks against hospitals, hospices, schools, universities, non-profit organizations, and government agencies.
CyberReason told Threatpost that it can’t say with 100-percent certainty that DarkSide is behind the attack, although “the characteristics of the attack are consistent with what we’ve seen with DarkSide,” a spokesperson said in an email.
…Or Was It Ryuk?
Ryuk meanwhile was first observed in 2018, as a variant of the Hermes 2.1 ransomware. But unlike Hermes, it’s not peddled on underground markets like the Exploit forum. Deloitte researchers have theorized that Ryuk is sold as a toolkit to attacker groups, which use it to develop their own “flavors” of the ransomware. There could therefore be as many variants as there are attacker groups that buy the code.
Ryuk has been increasingly prolific over time, spearheading double-extortion attacks where cybercriminals steal data on top of locking up files. In early 2021, it was estimated that Ryuk operators have raked in at least $150 million, according to an examination of the malware’s money-laundering operations. It also keeps improving; it recently added a self-propagation “worming” variant.
Click to enlarge. Source: Check Point.
Check Point Research pointed to reports that finger Ryuk ransomware as being behind the pipeline attack, as opposed to DarkSide. Ryuk is certainly a reasonable contender, given the massive number of victims it’s had just this year alone: Check Point puts it at more than 2,000. The U.S. is one of Ryuk’s favorite markets, Check Point told Threatpost on Monday: American organizations make up 15 percent of its efforts.
Bloomberg’s sources classified this as a double-extortion scheme, as in, besides encrypting files, the threat actors also stole data and threatened to leak it if the ransom isn’t paid.
Bloomberg reported on Saturday that the attackers actually began to steal Colonial’s data on Thursday, a day before triggering the ransomware attack itself, and said that they guzzled 100 gigabytes of data in just two hours on Thursday.
Is a Nation-State Cyberattacker at Work?
We don’t know enough to have definitive attribution yet, but there are interesting possibilities, according to Mike Hamilton, former CISO of Seattle and CISO of government cybersecurity firm CI Security.
“If Colonial is being extorted with ransomware it does not necessarily implicate organized crime, as nation-states have been known to obfuscate their motivation using ransomware as a false flag,” he told Threatpost on Monday morning. “If Colonial is NOT being extorted, this may be pure disruption for the purpose of creating further chaos in the American economy. This is a strategic interest of some countries, especially those that depend on energy for a good portion of their GDP; it is likely that energy prices will spike as a result of this action.”
Cyberactivism is another possibility, he suggested – such groups are increasingly using cyber-methods – but although pipelines are known to be targets for activists, they usually target pipelines under construction, he said.
Regardless of who’s behind the attack, it might wind up becoming designated as a terrorist act, he added. “These pipelines have been designated critical infrastructure,” Hamilton points out. “Intentionally disrupting or damaging these systems can be considered an act of terrorism. As more is learned about the event, and as the motivation of the actor(s) becomes clear, we’ll find out if this event has taken us from a cold to a much warmer cyber-conflict.”
All of that said, Adam Bixler, global head of third-party risk at cybersecurity firm BlueVoyant, told Threatpost on Monday morning that the attack doesn’t sound like the work of a nation-state. “The Colonial Pipeline vulnerabilities exposed to the internet, including open services on standard ports open to the internet, over the past few months are more than enticing for criminal groups indiscriminately scanning the internet. In light of the news that ransomware was the attack vector of choice, this is more than likely a monetarily motivated effort, likely excluding nation-state adversaries.”
Vulnerable Pipelines: An Industry With Dusty Cybersec
One thing’s for certain: Ransomware attacks on these types of targets are likely to become more frequent. John Cusimano, vice president at industrial cybersecurity company aeCyberSolutions, said that the industry is lagging in protecting critical infrastructure from the stranglehold of cyberattack.
“In our company’s extensive experience in assessing oil and gas pipelines for several of the country’s largest pipeline operators, we have found that pipeline cybersecurity is far behind that of other energy sectors (upstream and downstream O&G and electric utilities),” he told Threatpost in an email on Monday morning.
Click to enlarge. Source: Check Point.
Cusimano says that a common gap in the pipeline industry is the lack of segmentation of the pipeline supervisory control and data acquisition (SCADA) networks, which are the networks that connect the pipeline control center to every terminal, pumping station, remote isolation valve and tank farm along the pipeline.
These are sprawling networks covering extensive distances, but from a network segmentation standpoint, they’re flat, as in, once attackers gain access, there are no barriers, and they have access to every device on the network.
“While pipeline SCADA networks are typically separated from the company’s business (IT) networks with firewalls, by design, those firewalls pass some data between the networks,” Cusimano noted. “For example, network monitoring software, such as SolarWinds, may be permitted through the firewall in order to monitor the SCADA network. These permitted pathways through the firewall are one way malicious software or hackers can move from the IT network into the SCADA network. This was one of my greatest concerns when I learned of the SolarWinds attack.”
Another challenge with securing pipeline SCADA networks is that they branch into every facility along hundreds of miles of pipeline, Cusimano said. “Some of those facilities are in very remote places with little to no physical security, meaning that if an attacker breached the security of one of those facilities they could gain access to the network.”
Another complicating factor in securing pipelines: SCADA networks rely on extensive use of wireless communications such as microwave, satellite and cellular. “Breaching the wireless signals or stealing a cellular modem from a remote site could give an attacker access to the entire SCADA network,” Cusimano said.
An ‘Absolute’ and ‘Recurring’ Nightmare
Andrew Rubin, CEO and co-founder at Illumio, ssid that this could be “the most impactful ransomware attack in history, a cyber-disaster turning into a real-world catastrophe.”
It’s not only an “absolute nightmare,” he told Threatpost on Monday morning – it’s a recurring nightmare.
“Organizations continue to rely and invest entirely on detection as if they can stop all breaches from happening,” Rubin said. “But this approach misses attacks over and over again. Before the next inevitable breach, the President and Congress need to take action on our broken security model. This begins (but does not end) with the adoption of a zero-trust strategy. But instead of talking about and doing the hard work we need to do, we’ll watch the financial markets on Monday reward the entire security industry for failing to stop modern attacks from spreading into a disaster.”
According to the New York Times, gasoline prices rose as much as 4.2 percent early on Monday. By 9:30 a.m. EST, futures of gasoline for June delivery were up 1.6 percent: the highest level since late 2018. The outlet predicted that the instability is contained to prices that traders pay for gasoline, but we can expect it to ripple to prices at the pump in the coming weeks.
Expect More of the Same
Grant Geyer, chief product officer at industrial cybersecurity company Claroty, predicted that the attack against Colonial is just a teaser of future attacks.
“As cyber criminals and foreign adversaries seek opportunities for financial gain and power projection, our national critical infrastructure is an easy target,” he told Threatpost on Monday morning. “Industrial environments are operating with infrastructure that commonly maintains obsolete technology that can’t be patched, and staff that frequently are not as cyber-savvy as they need to be to keep attackers at bay. This leads to a situation where cybersecurity risk levels are below acceptable tolerances, and in some cases organizations are blind to the risk.”
He pointed to the water utility attack in Oldsmar, Fla. in February as being a case in point. “One additional risk factor of pipelines is that they are highly distributed environments, and the tools that are used to enable asset operators’ remote connectivity are optimized for easy access and not for security,” he said via email. ‘This provides attackers opportunities to sneak through cyber-defenses.”
Among critical infrastructure sectors, energy is especially at risk: Claroty’s researchers have found that the energy sector is one of the most highly impacted by industrial control systems (ICS) vulnerabilities, and that it experienced a 74 percent increase in ICS vulnerabilities disclosed during the second half of 2020 compared to two years prior.
Improving the nation’s critical infrastructure is going to require a public-private sector partnership, Geyer said, given the current gaps and potential risk to the U.S. supply chain and to national security.
Join Threatpost for “Fortifying Your Business Against Ransomware, DDoS & Cryptojacking Attacks” – a LIVE roundtable event on Wed, May 12 at 2:00 PM EDT. Sponsored by Zoho ManageEngine, Threatpost host Becky Bracken moderates an expert panel discussing best defense strategies for these 2021 threats. Questions and LIVE audience participation encouraged. Join the lively discussion and Register HERE for free.