Microsoft users are being targeted with thousands of phishing emails, in an ongoing attack aiming to steal their Office 365 credentials. The attackers add an air of legitimacy to the campaign by leveraging a fake Google reCAPTCHA system and top-level domain landing pages that include the logos of victims’ companies.
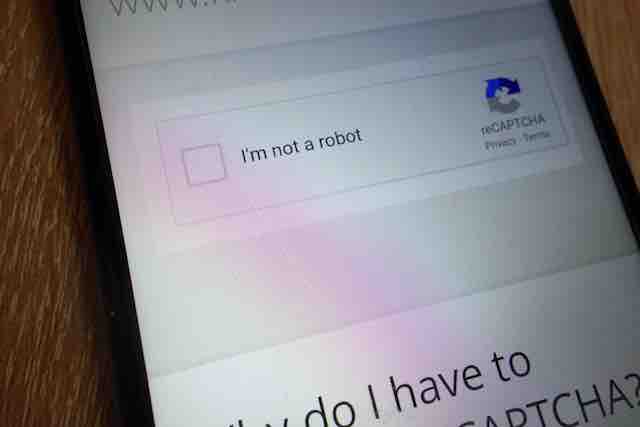
According to researchers, at least 2,500 such emails have been unsuccessfully sent to senior-level employees in the banking and IT sector, over the past three months. The emails first take recipients to a fake Google reCAPTCHA system page. Google reCAPTCHA is a service that helps protect websites from spam and abuse, by using a Turing test to tell humans and bots apart (through asking a user to click on a fire hydrant out of a series of images, for instance).
Once victims “pass” the reCAPTCHA test, they are then redirected to a phishing landing page, which asks for their Office 365 credentials.
“The attack is notable for its targeted aim at senior business leaders with titles such as Vice President and Managing Director who are likely to have a higher degree of access to sensitive company data,” said researchers with Zscaler’s ThreatLabZ security research team on Friday. “The aim of these campaigns is to steal these victims’ login credentials to allow threat actors access to valuable company assets.”
Fake Phishing Emails: Voicemail Attachments
The phishing emails pretend to be automated emails from victims’ unified communications tools, which say that they have a voicemail attachment. For instance, one email tells users that “(503) ***-6719 has left you a message 35 second(s) long on Jan 20” along with a lone attachment that’s titled “vmail-219.HTM.” Another tells email recipients to “REVIEW SECURE DOCUMENT.”
The phishing email sample. Credit: Zscaler
When the victims click on the attachment, they then encounter the fake Google reCAPTCHA screen, which contains a typical reCAPTCHA box – featuring a checkbox that the user must click that says “I’m not a robot,” which then triggers the turing test.
After filling out the fake reCAPTCHA system, victims are then directed to what appears to be a Microsoft login screen. The login pages also contain different logos from the companies which victims work at – such as one containing a logo from software company ScienceLogic and another from office rental company BizSpace. This reveals that attackers have done their homework and are customizing their phishing landing pages to fit their victims’ profile, in order to make the attack appear more legitimate.
Victims are asked to input their credentials into the system; once they do so, a message tells them that the validation was “successful” and that they are being redirected.
The phishing landing page mimics Microsoft’s login page. Credit: Zscaler
“After giving the login credentials, the phishing campaign will show a fake message that says ‘Validation successful,’” said researchers. “Users are then shown a recording of a voicemail message that they can play, allowing threat actors to avoid suspicion.”
Researchers found a variety of phishing pages associated with the campaign, which were hosted using generic top level domains such as .xyz, .club and .online. These top level domains are typically utilized by cybercriminals in spam and phishing attacks. That’s because they can be purchased for less than $1 each – a low price for adding a level of believability to phishing campaigns.
More Phishing Attacks on Fake Google reCAPTCHA Tactic
Credit: Zscaler
Adversaries have been leveraging bogus reCAPTCHA systems in their attacks for years. For instance, in 2019, a malware campaign targeted a Polish bank and its users with emails containing a link to a malicious PHP file, which eventually downloaded the BankBot malware onto victims’ systems. The attackers used a fake Google reCAPTCHA system to seem more realistic.
Another phishing attack in February purported to be sent from a voicemail service and contained a link to play the voice message “Play Audi Date.wav,” eventually redirecting victims to a malicious site with a reCAPTCHA message.
Both of the above examples show that reCAPTCHA continues to be used in phishing attacks, as the tactic successfully adds legitimacy to the attack: “Similar phishing campaigns utilizing fake Google reCAPTCHAs have been observed for several years, but this specific campaign targeting executives across specific industry verticals started in December 2020,” noted researchers.
Microsoft Office 365 users have faced several sophisticated phishing attacks and scams over the past few months. In October, researchers warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aimed to steal Office 365 recipients’ login credentials. Also in October, an Office365 credential-phishing attack targeted the hospitality industry, using visual CAPTCHAs to avoid detection and appear legitimate. Phishing attackers have also adopted new tactics like Google Translate or custom fonts to make the scams seem more legitimate.
Check out our free upcoming live webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community:
· March 24: Economics of 0-Day Disclosures: The Good, Bad and Ugly (Learn more and register!)
· April 21: Underground Markets: A Tour of the Dark Economy (Learn more and register!)