
Unknown hackers attempted to infiltrate Dragos, one of the leading industrial cybersecurity firms that works with government agencies and utilities globally, in a unsuccessful campaign that targeted the company’s executives and their family members, the firm said on Wednesday.
“We are confident that our layered security controls prevented the threat actor from accomplishing what we believe to be their primary objective of launching ransomware,” the company wrote in a blog post that said extortion attempts began on Monday and that no corporate systems or products were breached.
The hacking group did, however, gain access to the personal email address of a new sales employee before that person started working at the company. According to Dragos, the hackers began to pilfer general data from the Microsoft collaboration program SharePoint as well as 25 intelligence reports and customer support systems after logging into a new hire’s email account. One of those intelligence reports had an IP of a customer, the company noted. It’s not clear when the hackers breached the new hire’s email address.
“While the external incident response firm and Dragos analysts feel the event is contained, this is an ongoing investigation. The data that was lost and likely to be made public because we chose not to pay the extortion is regrettable,” Dragos said.
The hackers attempted to infiltrate several other portions of Dragos infrastructure such as the IT help desk and financial and marketing systems. Additionally, the attackers tried to access an employee recognition system and “sales leads,” the report said. The hackers were not able to access those systems due to role-based access control rules, the company said.
When Dragos did not respond to the extortion demands, the hackers began to target executives and their family members and others associated with the company, according to Dragos. One of the messages read: “They don’t care about you or your organization. Be like the hundreds of companies who’ve deal with us appropriately.”
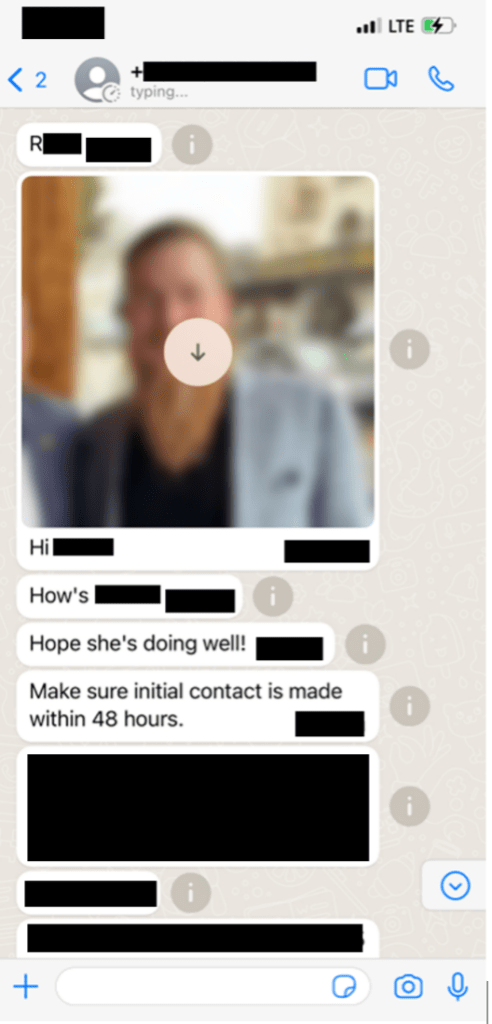
After Dragos continued to not engage, the criminals reached out to multiple known Dragos contacts “to elicit a response,” the company wrote. “Our decision was that the best response was to not engage with the criminals,” Dragos said.
A screenshot of a Telegram channel posted on Twitter by vx-undergound, the online malware repository, appears to be the actor that targeted Dragos although that has not been confirmed. The channel appears to have been created on Wednesday following Dragos’ blog post.
An unknown Threat Actor claims to have breached and exfiltrated data from Dragos pic.twitter.com/wckU28xEvA
— vx-underground (@vxunderground) May 10, 2023
The owner of the channel said that the incident was not a ransomware attack. The criminal hackers called Dragos a “criminal organization” that “instead of reaching a resolution” by paying the extortion demand the company “attempt to downplay an incident severely.”
The suspected hackers also claimed that the incident was not a ransomware attack and said they have access to more than 130 gigabytes of data pilfered from Dragos networks. So far, there has not been any evidence to show that claim is true.
Dragos’ public response to the attack and the company’s transparency generated praise from experts. Brain Harrell, former assistant secretary at DHS, said that “while there were no impacts to customers, this is a clear-cut example on how to isolate, mitigate, recover, and disclose.”
“Oftentimes, companies will go silent, circle the wagons, and refuse to be forthcoming when faced with a security concern,” he said. “With nation-state adversaries targeting the vendor communities that serve critical infrastructure, this transparency model is one for others to emulate when faced with an issue.”
The post Hackers attempt to extort Dragos and its executives in suspected ransomware attempt appeared first on CyberScoop.