After Bangkok Airways disclosed that it had been clobbered by a cyberattack last week, the LockBit 2.0 ransomware gang tossed its own countdown clock in the trash and went ahead and published what it claims are the airline’s encrypted files on its leak site.
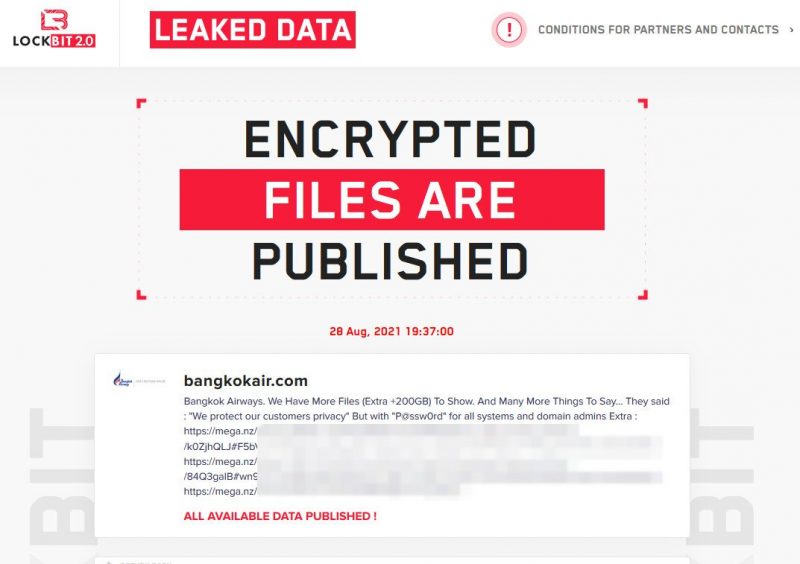
BleepingComputer posted an image (shown below) of LockBit’s “Encrypted Files Are Published” post, dated Saturday, Aug. 28, 19:37:00. That’s three days earlier than its original countdown clock: In that post, the ransomware-as-a-service (RaaS) gang promised that encrypted files would be published yesterday (Tuesday) if the airline didn’t pay the ransom. The sum of the demanded extortion hasn’t been reported.

Saturday’s LockBit post reads:
“Bangkok Airways. We Have More Files (Extra +200GB) To Show And Many More Things To Say … They said : We protect our customers privacy” But with P@ssw0rd for all system and domain admins Extra :”
The post included a series of redacted links.
Screen capture from LockBit 2.0’s leak site. Source: BleepingComputer.
The news outlet, which has been talking with the gang, reported that before LockBit went after Bangkok Airways on Aug. 23, the group also published encrypted files from another airline: Ethiopian Airlines.
The threat actor told the publication that the Accenture breach from earlier this month yielded the credentials used in both of the airline attacks. LockBit also claimed to have encrypted the systems of an unnamed airport using Accenture software.
UPDATE: After this article was published, Accenture reached out to Threatpost to deny LockBit’s claims. Its statement: “We have completed a thorough forensic review of documents on the attacked Accenture systems. This claim is false. As we have stated, there was no impact on Accenture’s operations, or on our client’s systems. As soon as we detected the presence of this threat actor, we isolated the affected servers.”
Bangkok Airways Breach
Bangkok Airways announced the breach last week, on Thursday, and LockBit 2.0 started a countdown clock the next day. In its initial post, the gang claimed to have stolen 103GB worth of compressed files that it would release yesterday, on Tuesday, and that they had a lot more – those +200GB of files it mentioned again in Saturday’s post – that they could add to the misery.
Bangkok Airways said at the time it disclosed the Aug. 23 attack that it’s working on beefing up its defenses.
The breach involved various personal data belonging to passengers, including:
The attackers evidently didn’t manage to access Bangkok Airway’s operational or aeronautical security systems, the company said in its public disclosure.
You Can’t Trust Countdowns
Ivan Righi, cyber threat intelligence analyst at digital risk protection provider Digital Shadows, pointed out to Threatpost that this is hardly the first time that LockBit has hit snooze or taken a hammer to its own countdown clock.
The gang repeatedly delayed its own threats in the Accenture breach, Righi noted, possibly because of its use of a clearweb site – Mega.nz, a cloud storage and file hosting service that’s known for offering the largest fully featured free cloud storage in the world, at 20GB. “The threat actor’s account on Mega was banned and the files are no longer accessible,” Righi noted.
With regards to LockBit’s premature ejaculation of Bangkok Airways’ files, Righi suggested that the group may have chosen to expose data earlier than scheduled “due to the risks of the files being taken down from Mega.”
Digital Shadows has identified 131 victims of LockBit 2.0 since the creation of the website in July 2021.
Oliver Tavakoli, CTO at AI cybersecurity company Vectra, observed that LockBit may have been motivated by Bangkok Airways’ public disclosure, given that attackers generally prefer for the attack not to be made public until after a ransom is paid: The delaying tactic provides one more pressure point to ensure that victims knuckle under. “Victims naturally want to assert as much control as possible, and disclosing the attack is a means to that end,” he told Threatpost on Wednesday.
Accenture Breach Could Spread Far More Ripples
Earlier this month, LockBit attacked Accenture, a global business consulting firm with an insider track on some of the world’s biggest, most powerful companies. It’s hardly surprising that airlines (and, going by what LockBit claimed, at least one airport) have apparently fallen prey to LockBit, given the cornucopia of credentials the gang presumably drained out of Accenture – a claim that, again, Accenture has dismissed.
Accenture’s clients include 91 of the Fortune Global 100 and more than three-quarters of the Fortune Global 500. According to its 2020 annual report, that includes e-commerce giant Alibaba, Cisco and Google. Valued at $44.3 billion, Accenture is one of the world’s largest tech consultancy firms, and employs around 569,000 people across 50 countries.
Depending on whether Accenture’s customers believe their security provider or LockBit, they might well be worried. The threat actor is claiming to have drained their security provider (a claim denied by Accenture), thus potentially compromising an untold number of its customers (if LockBit’s claims hold any water). Let’s hope that LockBit’s full of it and Accenture’s right about the threat actor not getting anywhere: According to a report released recently by Trend Micro, attacks in July and August have employed LockBit 2.0 ransomware that feature a souped-up encryption method: just one of many times it’s polished its arsenal.
Still, just because credentials (purportedly) stolen in the Accenture attack could potentially be used in future attacks shouldn’t be viewed as tantamount to future attacks being successful, Tavakoli told Threatpost. “Stealing credentials is often just the opening salvo to such an attack,” he said via email. “Organizations need to be more resilient to the next steps in these human-operated attacks. The move from a purely preventive mindset and to one of visibility, detection and response is a critical step in that journey.”
090121 14:26 UPDATE: Added input from Oliver Tavakoli and Ivan Righi.
090121 14:42 UPDATE: Added Accenture’s statement and updated story to reflect the fact that the company has denied LockBit’s claims to have siphoned its customers’ data.
Check out our free upcoming live and on-demand webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community.