Against the backdrop of widespread remote working and the increased use of collaboration apps, attackers are ramping up application-based attacks that exploit OAuth 2.0, Microsoft is warning.
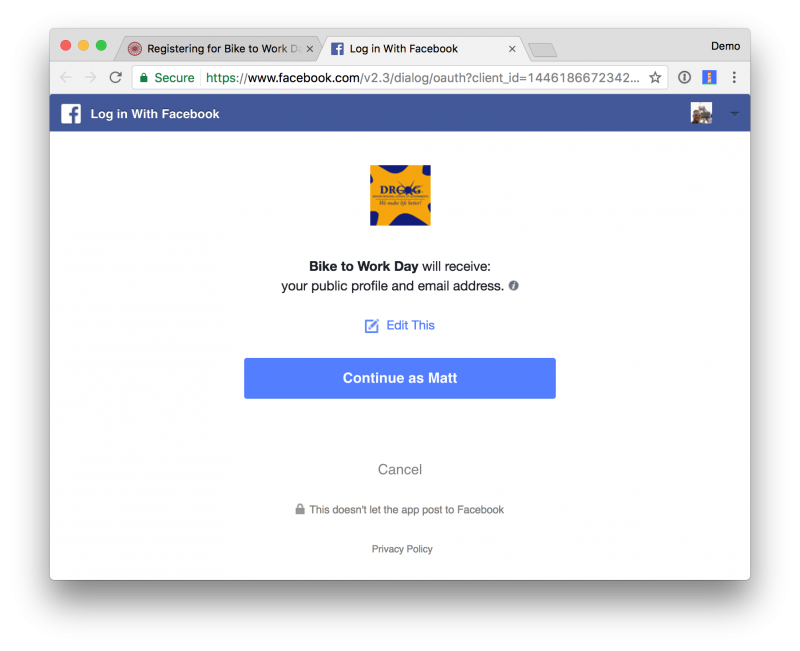
OAuth is an open standard for access delegation, commonly used as a way for people to sign into services without entering a password — using signed-in status on another, trusted service or website. The most visible example might be the “Sign in with Google” or “Sign in with Facebook” that many websites use in lieu of asking visitors to create a new account. These “Sign in” or “Log in” prompts are called consent prompts.
According to Agnieszka Girling, Partner Group PM Manager at Microsoft, consent phishing, a form of application-based attack that takes advantage of OAuth, is on the rise.
“This is where attackers trick users into granting a malicious app access to sensitive data or other resources,” she explained, in a blog post this week. “Instead of trying to steal the user’s password, an attacker is seeking permission for an attacker-controlled app to access valuable data.”
An offensive starts when an attacker registers a malicious app with an OAuth 2.0 provider, such as Microsoft’s own Azure Active Directory.
“The app is configured in a way that makes it seem trustworthy, like using the name of a popular product used in the same ecosystem,” explained Girling. “The attacker gets a link in front of users, which may be done through conventional email-based phishing, by compromising a non-malicious website or other techniques. The user clicks the link and is shown an authentic consent prompt asking them to grant the malicious app permissions to data.”
If a user clicks accept, they will grant the bad app permissions to access their credentials and potentially other sensitive data.
“The app gets an authorization code which it redeems for an access token, and potentially a refresh token,” Girling explained. “The access token is used to make API calls on behalf of the user. If the user accepts, the attacker can gain access to their mail, forwarding rules, files, contacts, notes, profile and other sensitive data and resources.”
Users can protect themselves by ensuring that whatever app they’re signing into is actually legitimate. They can also apply basic phishing-awareness strategies, such as looking for poor spelling and grammar in the original emails. Also, app names and domain URLs can offer red flags.
“Attackers like to spoof app names that make it appear to come from legitimate applications or companies but drive you to consent to a malicious app,” Girling said. “Make sure you recognize the app name and domain URL before consenting to an application.”
As remote working continues and collaboration apps such as Zoom, Webex Teams, Box and Microsoft Teams become ubiquitous, users are getting more and more used to cloud apps and signing into them using the OAuth function, Girling warned.
“The global pandemic has dramatically shifted how people work,” she said. “As a result, organizations around the world have scaled up cloud services to support collaboration and productivity from home…With increased cloud app usage and the shift to working from home, security and how employees access company resources are even more top of mind for companies.
BEC and enterprise email fraud is surging, but DMARC can help – if it’s done right. On July 15 at 2 p.m. ET, join Valimail Global Technical Director Steve Whittle and Threatpost for a FREE webinar, “DMARC: 7 Common Business Email Mistakes.” This technical “best practices” session will cover constructing, configuring, and managing email authentication protocols to ensure your organization is protected. Click here to register for this Threatpost webinar, sponsored by Valimail.