After going quiet for nearly a year, a potent hacking group with suspected links to the Israeli government reemerged online Monday, an indication that as the conflict between Israel and Hamas drags on, digital actors could play a greater role.
As the deadly violence between Israeli and Hamas fighters continues to unfold, the bulk of the fighting continues to be kinetic military operations. But since fighting began Saturday, a flurry of shadowy “hacktivist” groups on both sides of the conflict have knocked websites offline with distributed denial-of-service attacks, defaced some websites and triggered false alarms on mobile phone apps warning of incoming attacks.
The presence of state-backed hacking crews, hacktivist operations, pro-Iran information operations, and information operations linked to China indicate that the conflict between Israel and Hamas is likely to attract the attention of hacking crews and intelligence agencies around the globe.
“This crisis is too big to not draw in intelligence collectors from every corner,” John Hultquist, Mandiant’s chief analyst, told reporters Tuesday.
But it is the reemergence of Predatory Sparrow, which is believed to be a relatively sophisticated Israeli hacking operation with a history of destructive attacks in Iran, that has particularly caught the attention of students of cyber operations.
“It’s certainly a player to watch,” Hultquist said.
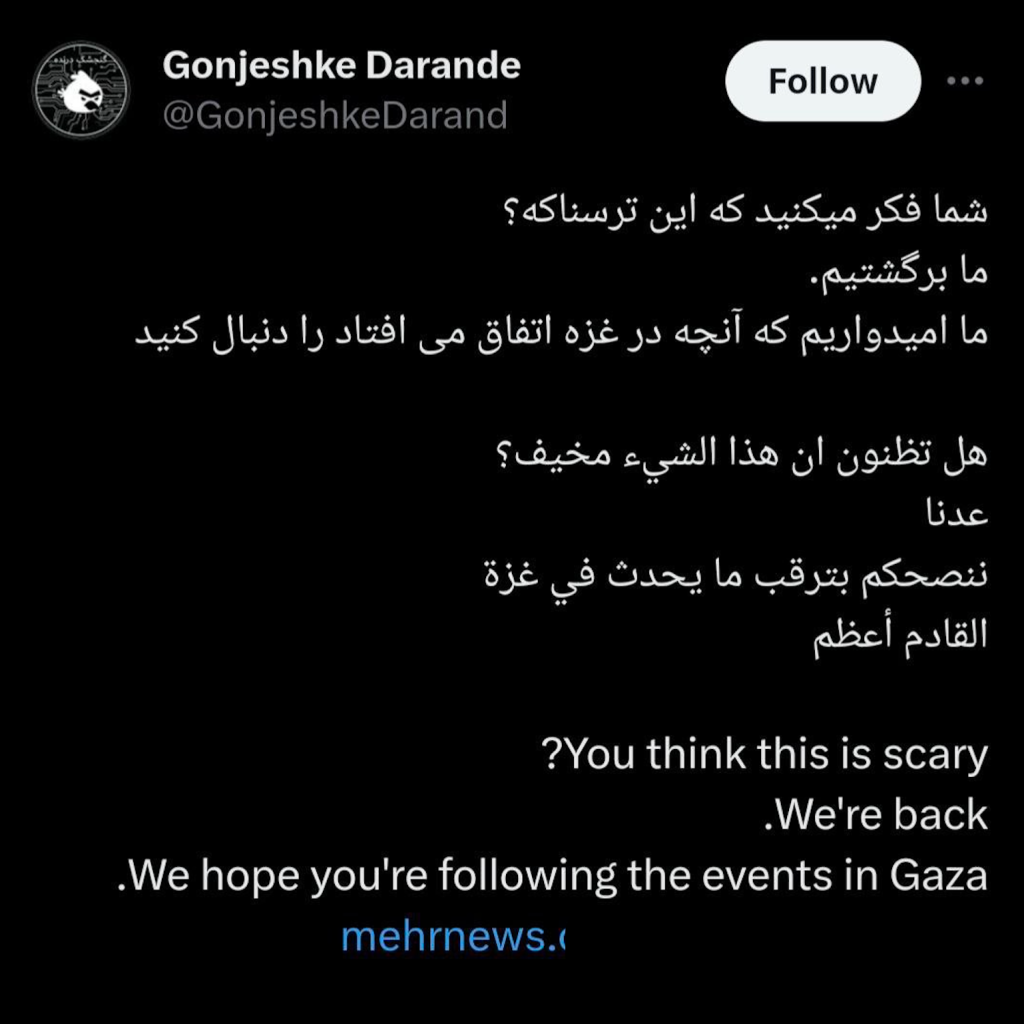
On Monday, Gonjeshke Darande — “Predatory Sparrow” in Persian — posted the first message to its Telegram channel since January, along with a similar post on X, formerly Twitter. “Do you think this is scary?” the group wrote in Persian, according to a Google Translation. “We returned. We hope you’re following what is happening in Gaza.”
The message included a link to the website of Iranian government’s Mehr News Agency, which had been temporarily made unavailable.
Between 2021 and 2022, analysts linked Predatory Sparrow to a string of high-profile attacks designed to embarrass the Iranian government. An attack in October 2021 on the payment system linked to a national network of fuel pumps in Iran disrupted the ability of Iranians to fill up and featured messages urging frustrated motorists to contact the office of Iran’s supreme leader. In June 2022, the group struck inside Iran again, targeting steel facilities they said were linked to the Islamic Revolutionary Guard Corps.
As part of the latter attack, the group released apparent closed circuit video showing heavy damage caused to one of the targeted facilities. The group appeared to have access to video monitoring inside the facility and timed the destructive attack to minimize the potential of injury to facility workers, leaving experts to surmise that the attack was highly strategic and professional.
“What makes Predatory Sparrow so brilliant is that each activity signals greater capabilities by virtue of their restraint,” Juan Andrés Guerrero-Saade, the senior director of SentinelLabs, told CyberScoop in an online chat. “‘We could’ve, but we didn’t, so don’t make us, cause we can.’”
“‘Hacktivist’ fronts temporarily taking down websites for headlines look like school children in comparison,” Guerrero-Saade added.
Predatory Sparrow did not respond to a request for a comment.
Predatory Sparrow has never claimed affiliation with any government, but anonymous U.S. defense officials told the New York Times that the operation targeting Iranian gas stations was carried out by Israel. There have been other hints of links to the Israeli government. After the attacks on steel facilities, for instance, the Times of Israel reported that Israeli military leaders had ordered an investigation into leaks and unauthorized disclosures boasting of the Israeli operation.
There are also indications that the Iranian government believes Predatory Sparrow to be an Israeli operation. In July 2022, a group calling itself “Homeland Justice” deployed destructive malware against multiple Albanian government systems in connection with that country’s hosting of a conference of the Mojahedin-e Khalq, an exiled dissident Iranian opposition group. In that operation, Homeland Justice — which multiple governments and private investigators linked to the Iranian government — used a logo mocking Predatory Sparrow’s Angry Bird-inspired branding featuring an irate bird inside a Star of David about to be snatched up by an eagle.

Among the groups active online amid the fighting between Israel and Hamas, Predatory Sparrow has the most prolific public record, but it’s far from the only one.
The hacking groups Killnet and Anonymous Sudan have said in their Telegram channels in recent days that they would attack the government of Israel and other targets, such as Israel’s Iron Dome missile defense system, although there’s no indication that attacks on such entities were successful. SiegedSec, a cybercrime group known more for its politically motivated attacks in the U.S. and around the world, said it was carrying out attacks on Israeli infrastructure in conjunction with Anonymous Sudan.
Anonymous Sudan is a group that emerged online in January 2023 with a string of DDoS attacks against multiple organizations in Sweden, according to the Swedish cybersecurity firm TrueSec. The company’s analysis suggests that the group likely has nothing to do with Sudan or Anonymous and that its use of paid infrastructure to carry out its attacks shows that it has “been carefully organized by someone willing to pay for it, not a spontaneous action by activists.”
Anonymous Sudan has cooperated in the past with Killnet, an overtly pro-Russian DDoS channel that has claimed a number of DDoS attacks around the world on perceived enemies of the Russian government as well as posted documents purportedly stolen from NATO, according to Mandiant.
“Most of the hacktivist groups that we are currently observing are primarily involved in defacements and DDoS attacks,” Oleg Dyorov, head of cybercrime investigations within the Group-IB Threat Intelligence unit, said of the operations his firm has observed amid the fighting in Israel.
“Only a handful of incidents, such as the one with the exploitation of an API vulnerability, can cause more significant harm and risks,” he added, referring to reports of an attack on the RedAlert app in Israel, which provides real-time alerts of rocket attacks for Israelis. In that incident, an attacker pushed false messages to some of the app’s users, including a warning that a nuclear bomb was incoming, according to Group-IB.
“Although many of these individuals possess limited technical expertise, the sheer size of their communities amplifies their impact,” Dyorov said in an email.
The post Savvy Israel-linked hacking group reemerges amid Gaza fighting appeared first on CyberScoop.