
A mobile phishing campaign that targeted customers of more than a dozen North American banks, including Chase, Royal Bank of Canada and TD Bank, managed to hook nearly 4,000 victims. The attacks used an automated SMS tool to blast bogus security text messages to mobile phone users between June and last month.
Mobile security firm Lookout identified the “mobile-first” phishing campaign and said that victims were sent text messages claiming that their bank detected suspicious activity tied to their account. The SMS-based messages each included a link to one of over 200 phishing pages.
“The [phishing pages] are built to look legitimate on mobile, with login pages mirroring mobile banking application layouts and sizing, as well as including links like, ‘Mobile Banking Security and Privacy’ or ‘Activate Mobile Banking,’” wrote Lookout researchers Apurva Kumar, staff security intelligence engineer and Kristin Del Rosso, senior security intelligence engineer, in a report published Friday.

 In their report, researchers pointed out that mobile-based phishing campaigns have advantages over their desktop equivalents. For one, mobile phishing messages and spoofed sites are less likely to be scrutinized, they said.
In their report, researchers pointed out that mobile-based phishing campaigns have advantages over their desktop equivalents. For one, mobile phishing messages and spoofed sites are less likely to be scrutinized, they said.
“Since mobile users are typically on the move and less likely to scrutinize the authenticity of an SMS message, text messages have become an attractive new attack vector,” researchers wrote.
Also, often a condensed mobile site will not display an entire URL, making it harder for a user to determine a site’s legitimacy.
Some of the banks impacted by the scam included; Scotiabank, CIBC, , Royal Bank of Canada, UNI, HSBC, Tangerine, TD Bank, Meridian, Laurentian, Manulife, BNC and Chase.
If hooked, victims were prompted to divulge answers to security questions such as their date of birth, credit-card expiration date, account number, username and password. Over the course of the seven-month campaign, researchers said, over 3,900 unique IP addresses (phones users) logged into one of the adversaries’ servers.
 “With the increase in multi-factor authentication for many apps, including those used for mobile banking, consumers are increasingly accustomed to banks communicating using SMS messages,” researchers wrote.
“With the increase in multi-factor authentication for many apps, including those used for mobile banking, consumers are increasingly accustomed to banks communicating using SMS messages,” researchers wrote.
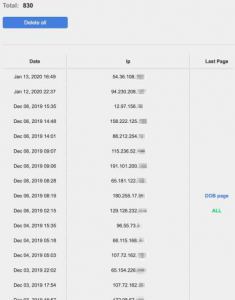
A traffic analysis of just one bogus mobile banking page revealed more than 800 unique clicks on the provided link sent via SMS. Lookout said that based on its research, it determined many victims followed the link, only answering a limited number of questions before abandoning the phishing attempt.
“A screenshot (see right image) from one phishing page highlights the IP addresses of the devices who clicked on the link, as well as how far into the phishing campaign they went (e.g., providing no information, making it to the ‘date of birth’ page, or fully completing the phish),” according to the report.
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join us Wednesday, Feb. 19 at 2 p.m. ET when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.