Hackers took over President Trump’s 2020 election campaign website late Tuesday, replacing parts of the site with a cryptocurrency scam before returning it to its original content several minutes later.
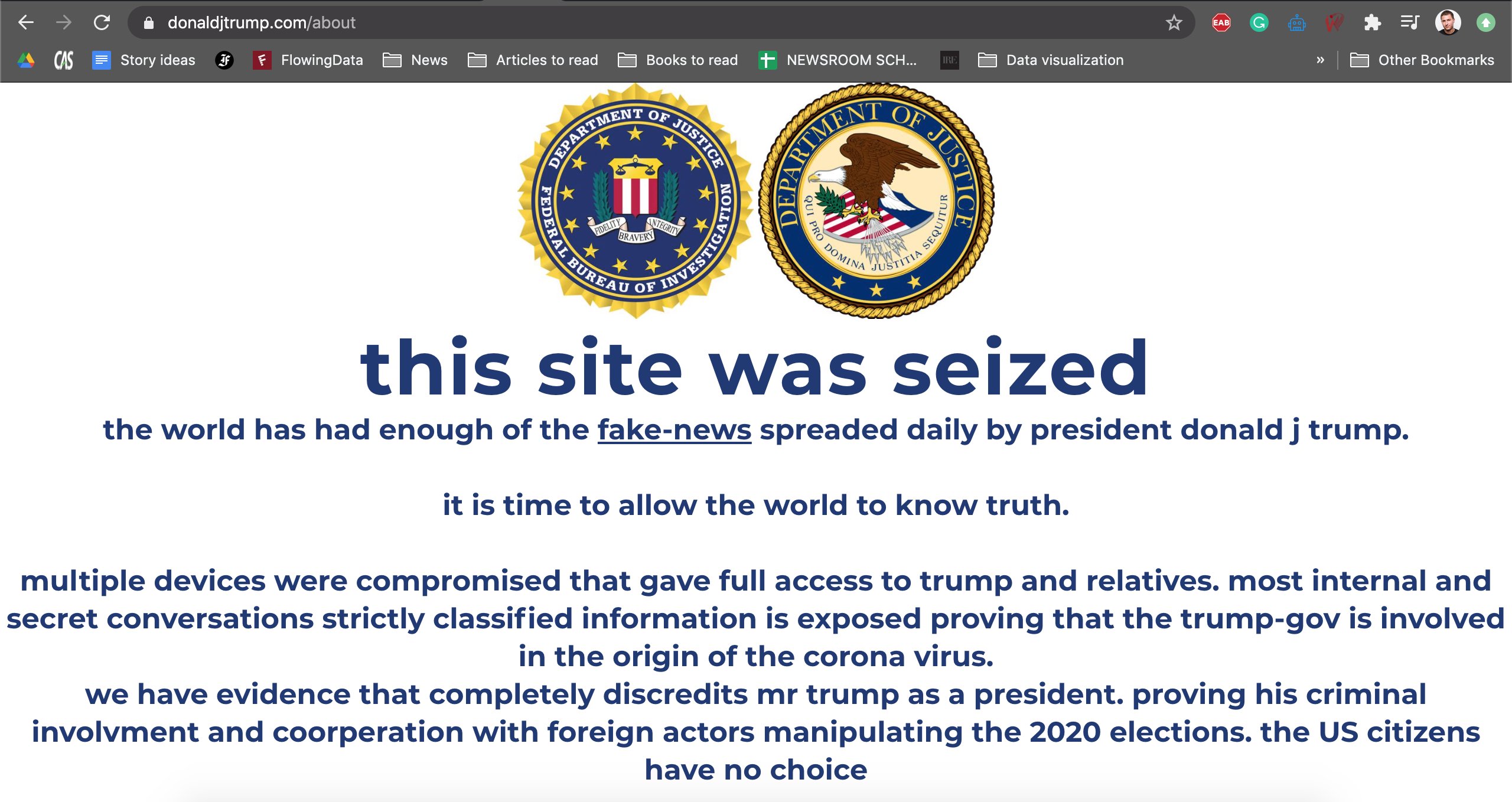
Journalist Gabriel Lorenzo Greschler was the first to notice the attack while he was doing research for a climate-change article, he wrote in a tweet. The accompanying photo showed a message proclaiming “this site was seized” and “the world has had enough of the fake news spread daily by president donald j trump [sic].”
While the hacked page claimed that the threat actors responsible compromised “multiple devices” that gave them “full access” to internal and secret conversations” of “trump and relatives,” there is no evidence that these statements are true, according to the Trump campaign.
 The hackers appeared to advocate the ousting of President Trump in the upcoming Nov. 3 election. They claim that the information they obtained prove that Trump and his government are “involved” in the original of the coronavirus as well as engaged in “criminal involvement and cooperation with foreign actors” that “completely discredits” the president. “The US citizens have no choice,” the hackers wrote.
The hackers appeared to advocate the ousting of President Trump in the upcoming Nov. 3 election. They claim that the information they obtained prove that Trump and his government are “involved” in the original of the coronavirus as well as engaged in “criminal involvement and cooperation with foreign actors” that “completely discredits” the president. “The US citizens have no choice,” the hackers wrote.
Following the message, attackers posted two addresses for Monero, a cryptocurrency oft used in nefarious cyber activities because it’s easy to send yet difficult to track. Indeed, research has found that illicit Monero-mining malware accounts for more than 4 percent of the XMR in circulation, and has created $57 million in profits for threat actors.
Journalist Gabriel Lorenzo Greschler was the first to notice the attack while he was doing research for a climate-change article.
The addresses allow people to basically buy access to the data with cryptocurrency, giving people the choice of whether they want the classified data shared or not.
“After the deadline we will compare the funds and execute the will of the world,” hackers wrote. “In both cases we will inform you.”
Hackers signed the page with a PGP public key linked to an e-mail address at planet.gov–a domain that does not exist—as a way for people participating in the scam to identify them.
The Trump campaigned acknowledged the hack late Tuesday, saying that the team is working with law enforcement to investigate the source of the attack and asserting that the attackers had zero access to classified data.
“There was no exposure to sensitive data because none of it is actually stored on the site,” campaign communications director Tim Murtaugh said in a statement published on his Twitter page.
One medical professional and Twitter user responded to Murtaugh’s tweet with doubt about the Trump administration’s overall capability to provide security and protection not just online but for the American people.
“If Trump can’t even secure his own campaign website, then how can he secure the country?” tweeted Dr. Eugene Gu, founder and CEO of CoolQuit. “If he can’t protect himself from the coronavirus, how can he protect everyone else? What a joke.”
The hack is not the first time threat attackers have targeted President Trump during the run up to next week’s election. Earlier this month, his Twitter account was allegedly accessed by Dutch ethical hacker Victor Gevers solely by guessing his password, “maga2020!.”
Meanwhile about a year ago, Microsoft researchers observed a group of hackers tied to Iran attempting to break into accounts associated with President Trump’s 2020 reelection campaign.
More attacks are likely to come in the countdown to the final day those eligible can cast their vote in the 2020 election, warned Chris Krebs, director of CISA.gov—the website for government’s Cybersecurity and Infrastructure Security Agency–on Twitter. Rather than targeting candidates, though, threat actors will likely try to attack voting infrastructure, he said.
“Things to keep an eye out for: this week & nxt are prime territory for visible, seemingly disruptive attempts to undermine confidence in voting systems,” Krebs tweeted. “Website defacements are superficial; Denial of Service attacks might deprive you of info, but won’t compromise the vote itself.”