
Researchers are warning of a new breed of Android malware, dubbed “Agent Smith,” that they claim has infected 25 million handsets in order to replace legitimate apps with doppelgangers that display rogue ads. The malware is tied to a China-based firm, according to Check Point researchers, and is targeting users in India, Pakistan and other parts of Asia.
According to research released Wednesday, the malware targets phones that have not been patched for a host of old vulnerabilities such as Janus, an Android flaw that dates back to 2017. Victims are enticed to download dropper program camouflaged as either an image editor, porn-related app or game from a third-party app store. The dropper program then downloads the Agent Smith payload.
For those victims with unpatched phones who download apps from third-party app stores, things go from bad to worse. “The core malware is usually disguised as Google Updater, Google Update for U or ‘com.google.vending’. The core malware’s icon is hidden.”

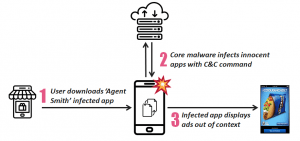 The malware inspects the apps on the targeted phone, and then fetches updates to “patch” recognized APKs with malicious ad modules. To do this, the attackers rely on the Janus vulnerability (fixed by Google in December 2017), which allows the threat actors to bypass Android’s APK integrity checks and replace any application on its “prey list” with an infected version.
The malware inspects the apps on the targeted phone, and then fetches updates to “patch” recognized APKs with malicious ad modules. To do this, the attackers rely on the Janus vulnerability (fixed by Google in December 2017), which allows the threat actors to bypass Android’s APK integrity checks and replace any application on its “prey list” with an infected version.
Check Point estimates that each victim could have as many as 112 apps replaced on their handsets with ones that display the rogue ads.
“Upon kill-chain completion, Agent Smith will then hijack compromised user apps to show ads,” they wrote. “In certain situations, variants intercept compromised apps’ original legitimate ads display events and report back to the intended ad-exchange with the Agent Smith campaign hacker’s ad IDs.”
Check Point said that the Agent Smith dropper proliferates via third-party app store called 9App, patronized primarily by Indian (Hindi), Arabic and Indonesian users.
Researchers believe the threat actors behind the malware is a China-based organization located in Guangzhou, a large city located northwest of Hong Kong, based on analysis of the Agent Smith command-and-control servers.
“We connected the Agent Smith campaign to a Chinese internet company located in Guangzhou whose front end legitimate business is to help Chinese Android developers publish and promote their apps on overseas platforms,” researchers wrote.
They added, “We started with most frequently used C&C domains ‘a***d.com’, ‘a***d.net’, and ‘a***d.org’. Among multiple sub-domains, ‘ad.a***d.org’ and ‘gd.a***d.org’ both historically resolved to the same suspicious IP address.”
Google’s most recent version of its Android OS is Pie, version 9.0. Check Point reported that Agent Smith is most prevalent in phones running Android version 5.0 (40 percent) and version 6.0 (34 percent), with 9 percent of infected phones running version 8.0.
“The Agent Smith campaign serves as a sharp reminder that effort from system developers alone is not enough to build a secure Android ecosystem,” researchers wrote. “It requires attention and action from system developers, device manufacturers, app developers and users, so that vulnerability fixes are patched, distributed, adopted and installed in time.”