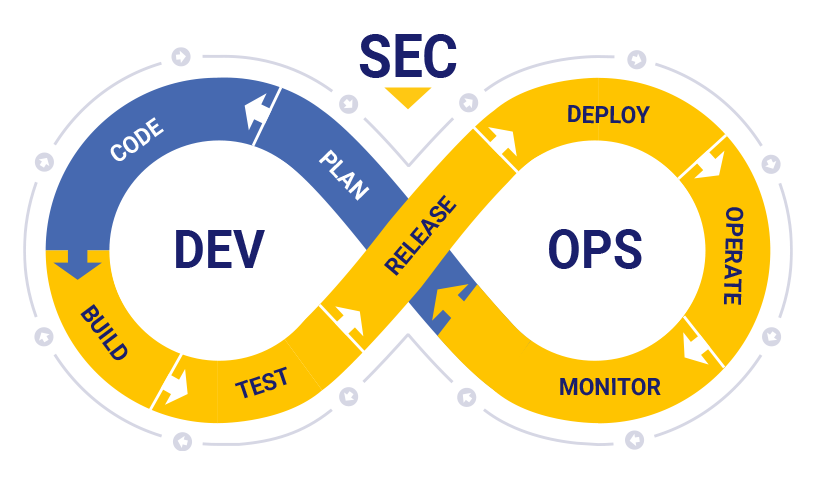
Security should never be an afterthought when developing software and applications. However, as technological advances continue to take hold, the security tools many rely on are changing in real-time, and combatting potential breaches or hacks of your wares before they arise now requires new strategies. To stay one step ahead of bad actors, it’s time to reimagine the application-development process from “DevOps” to “DevSecOps.”
DevOps is an evolution of the agile development lifecycle for software that bridges the gap between development and operations teams. It breaks down silos and increases an organization’s ability to deliver applications and services faster than traditional software-development models. Previously, the traditional “waterfall method” required long cycles upfront and resulted in strenuous and tedious processes – and by the time these solutions were deemed ready for release, the market had likely changed.
Today, agile software teams have release cycles that are a matter of days or hours, which increases the risk of making mistakes and introducing vulnerabilities. So, how can organizations produce more secure code and applications when working at breakneck speeds, and thwart potential cyberattacks when they do not yet know what those attacks look like? To bolster cybersecurity for their products, solutions and partners, a company must shift from a DevOps culture to “DevSecOps” culture.
Start Secure, Stay Secure
DevSecOps puts security at the forefront of the development process as a whole, ensuring that good cyber-hygiene remains top-of-mind for developers and operators from start to finish. This shift in mindset encourages organizations to find the best possible approaches to developing secure code and applications – and there are a variety of resources and strategies to help development teams do exactly that.
Here are some of the most important:
Why Third-Party Libraries Are Your Responsibility
Third-party libraries like Apache Struts, Telerik UK (a third-party .NET library) and others are considered both a blessing and a curse for organizations. On the one hand, organizations can leverage work built by others, adapt it and create more rich experiences on top of it, allowing them to bring their expertise without having to make everything from scratch. On the other hand, continued updates and upgrades of the libraries is required to maintain a clean code base. It’s easy to import malicious code from code repositories, too.
Developers will need to update toolkits to ensure third-party materials have their vulnerabilities patched regularly and in real-time, because even the most minor oversights by your team or your partners can result in the most significant breaches. In fact, the Cybersecurity and Infrastructure Security Agency (CISA) recently released a list of the most-exploited software vulnerabilities and Apache Struts was the second-most attacked technology on the list.
Attackers also often exploit vulnerabilities in open-source web services, such as Apache Tomcat, which is bundled in an untold number of products.
The Ongoing Game of Whack-a-Mole
Threats and attack styles that do not exist today will attempt to exploit vulnerabilities in your systems tomorrow. However, by placing security at the forefront and implementing a DevSecOps culture, organizations are better positioned to mitigate threats as they appear – and before they cause any issues or interruptions.
The next wave of threats is coming. Is your organization prepared?
Phil Richards is CSO at Ivanti.
Enjoy additional insights from Threatpost’s InfoSec Insider community by visiting our microsite.