Researchers at the security firm Palo Alto Networks worked with domain registrar and web hosting firm GoDaddy to shut down 15,000 subdomains pitching ‘snake oil’ products and other scams. The takedowns are linked to affiliate marketing campaigns peddling everything from weight-loss solutions and brain-enhancement pills.
Those behind the spam campaigns used a technique called domain-shadowing, and they were able to compromise thousands of servers and abuse hundreds of domains and website admin account credentials, according to researchers.
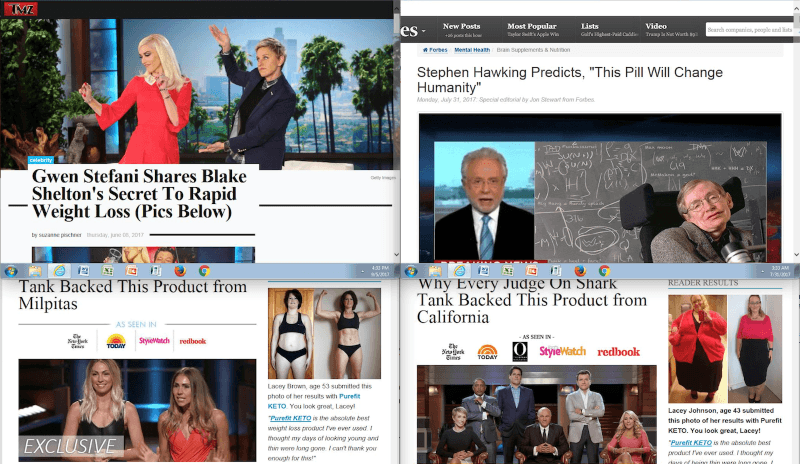
Spam campaigns associated with these subdomain takeovers date back to 2017. Links in messages pointed to subdomains of websites, which unknowingly hosted the product pitches that were backed by bogus endorsements purporting to be from the likes of Stephen Hawking, Jennifer Lopez and Gwen Stefani.
“On a scale of one to 10 for the ‘worst types of spam’ you can receive, approaching that perfect 10 score is spam related to ‘snake oil’ products that are so patently fake that you struggle to understand why they would even bother trying to sell it,” wrote Jeff White, senior threat researcher at Palo Alto Networks, in a blog post outlining the takedown.
Example of a “farticle” extolling the merits of a dubious pill, solution or potion. Farticle is a term used to describe a fraudulent article. (Click to Enlarge)
White investigated and traced the links in the spam messages to an elaborate URL redirection chain that eventually dumped users on the fake products’ landing pages. The redirections, researchers discovered, were leveraging compromised servers. To help obfuscate the sketchy behavior, spammer also used a Caesar cipher (a simple substitution code) and a hypertext preprocessor (PHP) file for handling the redirections.
“The [Caesar cipher] injection is using .php files on compromised sites to drive traffic to fraudulent and/or scam pages,” according to a researcher at PassiveTotal that White consulted with during his investigation. “[These included] fake tech support and fake sites purporting to be news sites, reporting on the incredible effects of weight-loss and intelligence pills.”
Next, White determined that the redirection sites and those that hosted the spam pitches were using legitimate registrant accounts in a technique called domain-shadowing. That’s when attackers use stolen domain registrant credentials to create massive lists of subdomains, which are used in quickly rotating fashion to either redirect victims to attack sites, or to serve as hosts for malicious payloads. This technique is considered an evolution of fast-flux, where malicious elements are moved from place to place rapidly, in an effort to stay ahead of detection.
“It would seem likely that the person(s) behind [the campaigns] were going about it in an automated fashion, logging into these legitimate domain accounts and using a dictionary of simple English words to create subdomains pointing to their redirector,” said the researcher.
This isn’t the first time GoDaddy has had to deal domain-shadowing used to link to malicious activity. Over the years the approach has been used to distribute everything from the Angler Exploit Kit to the RIG Exploit Kit.
While in White’s case the payload wasn’t malware, but rather affiliate marketing scams, he warned of the malicious nature of those behind the spam campaigns: “There are a lot of players in the affiliate marketing world, from the affiliates to the merchants and all of the networks in-between,” he said. “Hopefully this blog helps to shine some light on how at every link in this chain there are shady, sometimes illegal and almost always deceptive business practices still being employed, to scam hard working people out of their money.”