Mac users are being targeted by trojanized cryptocurrency trading apps, which once downloaded actually drain victims’ cryptocurrency wallets, researchers warn.
The four fake applications in question, Cointrazer, Cupatrade, Licatrade and Trezarus, claim to be rebranded copies of an actual cryptocurrency trading application offering called Kattana. The actors behind the campaign used websites that copy Kattana’s legitimate website to convince unwitting cryptocurrency enthusiasts to download the fake apps. The bogus websites include a download button, with a link to a ZIP archive containing the trojanized application bundle.
“For a person who doesn’t know Kattana, the websites do look legitimate,” said Marc-Etienne M. Léveillé, senior malware researcher with ESET, in an analysis last week. “Not only did the malware authors wrap [copies of] the original, legitimate application to include malware; they also rebranded the Kattana trading application with new names and copied its original website.”
Once downloaded, the trojanized apps in question deploy malware called GMERA to collect victims’ browser information (including their cookies and browsing history), access and drain their cryptocurrency wallets and take screenshots of their devices.
GMERA was previously uncovered by researchers with Trend Micro, who in September 2019 said the malware was being spread via trojanized cryptocurrency apps in a separate campaign, leveraging malicious versions of the trading app Stockfolio.
Malicious Apps
This most recent campaign has evolved to use new, rebranded apps, researchers said – however, “as in the previous campaigns, the malware reports to a [Command and Control] server over HTTP and connects remote terminal sessions to another [C2] server using a hardcoded IP address.”
The four apps in question have minor differences, but the functionalities are generally the same, researchers said. In a deep-dive of the Licatrade sample, researchers found that the application bundle includes a shell script (run.sh), which once downloaded launches and attempts to set up persistence on the victims’ system by installing a Launch Agent.
 However, “it’s interesting to note that persistence is broken in the Licatrade sample: the content of the resulting Launch Agent file (.com.apple.system.plist) isn’t in Property List format as launchd expects, but instead is the command line to be executed,” said Léveillé.
However, “it’s interesting to note that persistence is broken in the Licatrade sample: the content of the resulting Launch Agent file (.com.apple.system.plist) isn’t in Property List format as launchd expects, but instead is the command line to be executed,” said Léveillé.
The last line of the shell script sets up a reverse shell to the operators’ server, which then allows attackers to send out the various malicious commands to the malware.
Licatrade was signed using a certificate with the common name field set to “Andrey Novoselov” and using developer ID M8WVDT659T. The certificate was issued by Apple on April 6, 2020, and revoked the same day that researchers notified Apple of the malicious application.
Researchers believe that this campaign started on April 15, 2020, as that was the date on both the modification timestamps of the files in the ZIP archive, the date the application was signed, and the last‑modified HTTP header when they downloaded the archive.
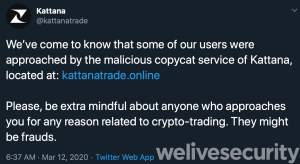
Switzerland-based Kattana has also previously warned of malicious, rebranded apps, posting a warning on Twitter suggesting that its users were “approached” individually to lure them into downloading a “malicious copycat service” of its software.
We’ve come to know that some of our users were approached by the malicious copycat service of Kattana, located at: https://t.co/paSARVJPPZ
Please, be extra mindful about anyone who approaches you for any reason related to crypto-trading. They might be frauds.
— Kattana (@kattanatrade) March 12, 2020
When asked for comment, a Kattana spokesperson told Threatpost that the company is aware of this campaign. “We have informed our users about this malicious activity in our official communication channels,” the spokesperson told Threatpost.
Catalina macOS Avoided
Researchers also noted that once downloaded, the malware checks to see whether the system is running Catalina, the most recent version of macOS, before it attempts to take a screenshot of the device. Researchers believe that’s because Catalina added a feature where recording the screen or taking a screenshot must be approved by the user for each application – which would be a red flag to the Mac user.
“The fact that a screenshot should not be taken on Catalina and that an obvious warning sign will be displayed on the operator’s terminal made us wonder why they act differently on the current macOS version,” said Léveillé. “We tested taking a screenshot from the reverse shell on Catalina and ended up with [a] warning in our sandbox, which is rather suspicious considering a trading application has no business doing so.” [See image to the left]
Hacks, malware and scams that leverage cryptocurrency trading are ballooning, researchers warn. Last week, in fact, Twitter locked down thousands of verified accounts belonging to high-profile Twitter users after hackers perpetrated a massive cryptocurrency scam on its platform. Tweets sent from those hijacked accounts each promoted an advance fee cryptocurrency scam, promising to double the value of Bitcoin currency sent to one specific wallet.