
Researchers are warning of an increase in phishing emails that use YouTube redirect links, which help attackers skirt traditional defense measures.
If certain malicious URLs are blocked by web browser phishing filters, attackers commonly use a redirector URL to bypass these filters and redirect the victim to their phishing landing page. URL redirects have been used in previous campaigns, including malicious redirect code affecting Joomla and WordPress websites and HTML redirectors being used by Evil Corp. Now, a new campaign is using legitimate YouTube redirect links.
“Most organizations allow the use of platforms such as YouTube, LinkedIn, and Facebook and whitelist the domains, allowing for potentially malicious redirects to open without any fuss,” said researchers with Cofense, in a Wednesday post.”
Researchers said that the emails using this method originated from a fraud domain, sharepointonline-po.com, which was recently registered, on Feb. 19. The attackers purported to be with SharePoint, a web-based collaborative platform that integrates with Microsoft Office. The email indicated that a new file has been uploaded to the target company’s SharePoint site, and included an option to “View File.”
When a user hovers their mouse over the “View File” URL, they see a seemingly-legitimate embedded YouTube link (hXXps://www[.]youtube[.]com/redirect?v=6l7J1i1OkKs&q=http%3A%2F%2FCompanyname[.]sharepointonline-ert[.]pw).
“Although the email may appear illegitimate to a trained ey””A curious or unsuspecting end user may click the button expecting to see a legitimate file,” said researchers.
When they click on the URL, victims are redirected to YouTube, and then immediately redirected to another link (companyname[.]sharepointonline-ert[.]pw), which is the final phishing landing page.
“So far, all phishing links from this campaign utilize some variation on sharepointonline-ert[.]pw, specifically sharepointonline-xxx followed by a variation of three letters, with the top-level domain always being .pw,” said researchers. “Each of these fraud domains are quickly registered with Namecheap and used for this campaign, which suggests the possibility of bot automation.”
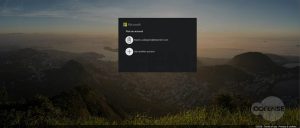 The phishing landing page itself is hosted on a legitimate Google page (googleapis.com), which means its certificate is verified (presumably by Google) – helping the page appear more legitimate: “Use of this legitimate website allows the threat actor to sneak by any Secure Email Gateways (SEGs) or other security controls,” researchers stressed.
The phishing landing page itself is hosted on a legitimate Google page (googleapis.com), which means its certificate is verified (presumably by Google) – helping the page appear more legitimate: “Use of this legitimate website allows the threat actor to sneak by any Secure Email Gateways (SEGs) or other security controls,” researchers stressed.
This page purports to be a typical Microsoft branded login page. The recipient email address is appended within the URL, which automatically populates the login box with the account name. While the login page is attacker-controlled, and passwords that are entered are sent to the threat actor, nothing appears amiss with the page – in fact, it is almost a perfect replica, researchers said.
“The main differences are: The box surrounding the login is black instead of white; the small detail of the banner at the bottom has different information than Microsoft’s actual login; and the copyright year is showing as 2019,” they said.
Attackers continue to raise the bar when it comes to phishing attacks. More recently they have been spotted tapping into the panic around the coronavirus with spear-phishing emails; and, attackers are also using anything from taxes to real estate decoys – and even HIV test results – to convince victims to hand over their credentials.
Interested in security for the Internet of Things and how 5G will change things? Join our free Threatpost webinar, “5G, the Olympics and Next-Gen Security Challenges,” as our panel discusses what use cases to expect in 2020 (the Olympics will be a first test), why 5G security risks are different, the role of AI in defense and how enterprises can manage their risk. Register here.