
A software vulnerability is a weakness in an operating system or application that can be exploited by an attacker to invade an IT network. When publicly disclosed, these software vulnerabilities are usually assigned a CVE identifier. CVE is a popular term when referring to a vulnerability, and 50 to 60 CVEs are discovered every day on average.
Clearly, vulnerabilities are increasing rapidly, challenging IT security teams. Furthermore, over 40% of discovered vulnerabilities have no CVE identifier assigned and can be easily exploited by cybercriminals. These vulnerability loopholes allow unauthorized access to the network, resulting in ransomware and malware attacks.
IT Security teams must implement a seamless vulnerability management process to prevent cyber attacks. They should continuously identify the vulnerabilities in their network, assess them thoroughly, prioritize them based on their severity, remediate them with relevant patches, and report all the data for strategic analysis.
It’s evident that CVEs or software vulnerabilities are a critical security loophole, but are these the only form of vulnerabilities attackers’ look out for? To answer this, we need to rethink vulnerabilities from the standpoint of an entire attack surface.
Are Software Vulnerabilities the Only Vulnerability in the Attack Surface?
CVEs or software vulnerabilities contribute only to a part of security risks in the IT vulnerability landscape. The attack surface comprises numerous vulnerabilities from a misconfigured firewall policy, unavailability of antivirus, unauthorized applications, lack of visibility over scheduled tasks, unwanted services and ports, hidden assets, and publicly discoverable files to numerous security control deviations and anomalies.
All these vulnerabilities and security risks are as threatening as a software vulnerability and can easily open gateways for an array of cyberattacks. IT security teams should look beyond CVEs and software vulnerabilities and start managing these security risks to attain a strong security posture and combat attacks.
Top Security Risks in the IT Security Landscape
Here are the top security risks that are as threatening as a software vulnerability and need to be considered as a vulnerability in the IT security landscape.
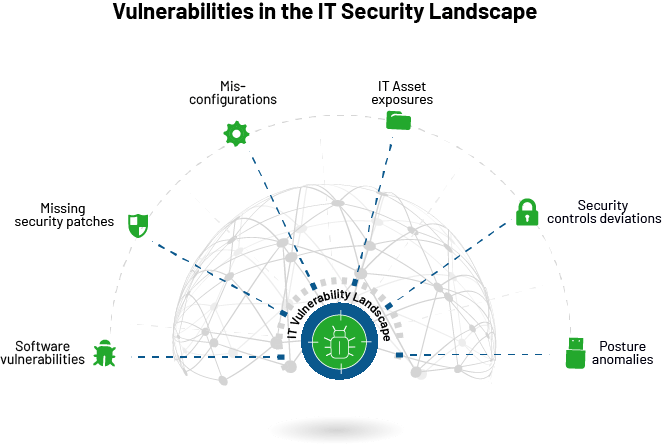
Like the above security risks, security deviations and posture anomalies are present in an IT infrastructure that are as alarming as a software vulnerability. Attack surface reduction cannot be achieved only by managing CVEs. All the vulnerabilities and security risks discussed above must be managed rigorously to minimize attack surfaces and combat cyberattacks.
Again, opting for different solutions to manage all these vulnerabilities and security risks will only create chaos and complexities. IT security teams should start looking for a solution that automatically detects and remediates vulnerabilities, IT asset exposures, misconfigurations, security control deviations, and posture anomalies from a single place. Only a tool that treats all these vulnerabilities equally can meet today’s IT security demands and pave the way for a threat-free IT landscape.
[FREE On-demand Event: Join Keeper Security’s Zane Bond in a Threatpost roundtable and learn how to securely access your machines from anywhere and share sensitive documents from your home office. WATCH HERE.]